Overview
On May 28, 2025, Scania, a leading Swedish manufacturer of heavy trucks, buses and a member of the Volkswagen Group, fell victim to a security incident that started quietly but quickly turned into an extortion campaign. Attackers exploited credentials belonging to an external IT partner to gain unauthorized access to Scania’s insurance claims portal, downloading thousands of sensitive documents.
But this wasn’t just another data leak, it became a targeted extortion attempt, with employees directly contacted by the attackers via encrypted email services. This incident adds to the growing wave of breaches that leverage third-party access and stolen credentials as their entry point.
What Happened?
Here’s a breakdown of the timeline and nature of the attack:
- May 28–29 – Attackers used login credentials belonging to an external IT provider to access Scania’s insurance claim management system.
- Data exfiltration – Over 34,000 files and scanned forms were stolen. These likely contain names, ID numbers, addresses, financial details, and medical information tied to vehicle insurance claims.
- May 30 – The threat actors began contacting Scania staff using ProtonMail accounts, threatening to release the data unless their demands were met.
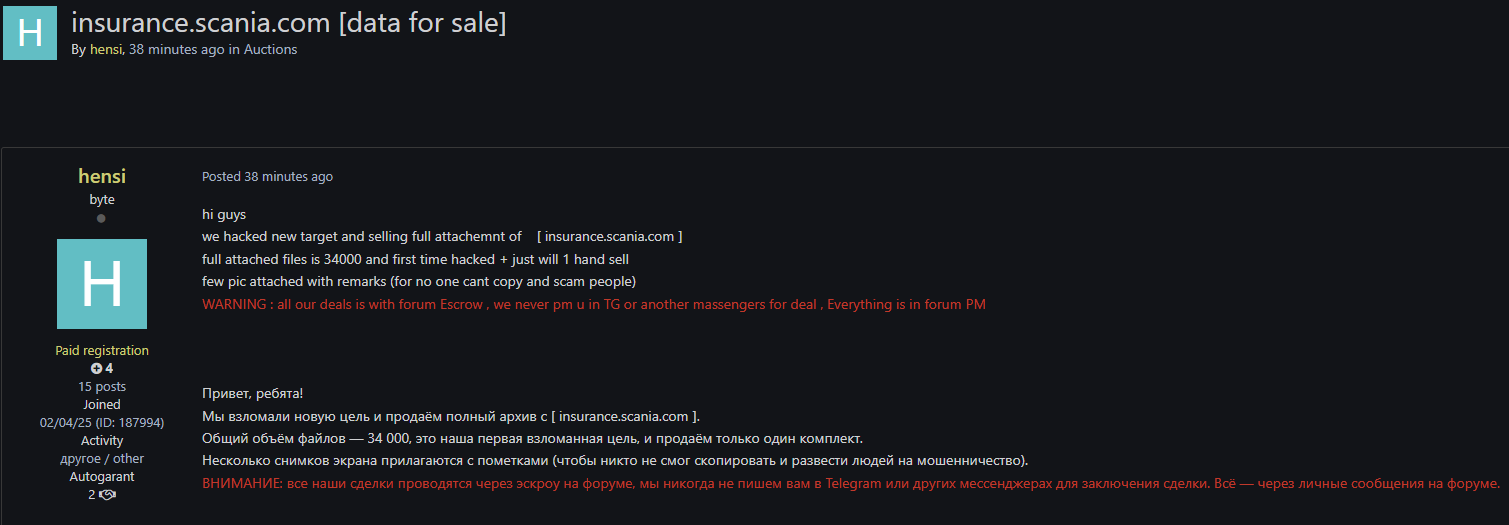
Screenshots of the files appeared on underground forums shortly after, and one attacker offered “exclusive access” to the data in a post signed by “hensi”.
How It Happened?
The attackers used stolen third-party login credentials to access Scania’s insurance system. based on early analysis and threat intel, here’s what likely happened:
- Third-Party Access Exploitation – The attackers exploited stolen credentials not from Scania’s core infrastructure but from a third-party IT supplier managing part of their insurance platform. This highlights the risks existing in supply‑chain security.
- Infostealer Malware – Analysis suggests the credentials were probably harvested using Infostealer malware, infostealers often harvest tokens, cookies, and saved credentials from infected machines.
- Data Exfiltration – Once in, they exfiltrated insurance claim documents, likely containing sensitive personal, financial, and potentially medical data.
- Extortion phase – The attackers escalated from theft to blackmail, aiming to monetize stolen information by pressuring Scania and selling data samples.
Impact
While Scania described the overall business impact as “limited,” the breach raises several concerns:
- Privacy Exposure -Personal, financial, and possibly medical information was part of the 34,000+ files leaked. Even if not “widely” exposed yet, the files are in criminal hands.
- Reputational Risk – Scania operates globally and is part of the Volkswagen Group. Any public data mishandling even via a partner can trigger regulatory investigations and erode trust.
- Regulatory Fallout – Regulatory bodies may impose fines or compliance mandates, especially if data belonging to EU citizens was impacted.
Recommendations
- Supply-chain hygiene – Enforce strict vendor risk assessments and continuous monitoring for third-party partners.
- Monitor for anomalies – Implement real-time detection of unusual data exports and access patterns.
- Encrypt sensitive data – Ensure all critical data, especially personal, are encrypted in transit and at rest.
- Credential Management – Audit for exposed secrets, deploy credential vaulting, and rotate partner access regularly.
Conclusion
The Scania data breach is an example of how a single compromised partner can open the door to a damaging chain of events. Just one infostealer, one set of stolen credentials, and a trusted connection that was taken for granted.
This incident reminds us that even trusted partners can become security risks if their access isn’t managed carefully. It’s not just about protecting your own systems anymore; it’s about keeping a close eye on how others connect to them.
At the end, breaches like this are preventable. Stronger identity controls, better monitoring, and clear boundaries with vendors can make all the difference.
