In today's complex enterprise environments, Non-Human Identities (NHIs) significantly outnumber human users. These service accounts, applications, and automated processes often operate with elevated privileges and, more critically, can be granted the authority to request access for other NHIs. This creates intricate delegation chains that introduce unique security challenges often overlooked in traditional identity governance frameworks.
The Invisible Network of Machine Identities
When Application A can request temporary credentials for Microservice B, which can then provision access for Database Daemon C, a delegation chain forms. These chains frequently grow organically as systems evolve, creating an invisible network of trust relationships that security teams struggle to map and monitor.
Recent data breaches highlight this vulnerability - attackers don't target the most secure systems directly. Instead, they compromise a seemingly insignificant NHI with delegation authority, using it as a stepping stone to gradually elevate privileges through established trust relationships.
The Trust Radius Concept
One innovative approach to addressing this challenge is implementing the "Trust Radius" concept. Unlike traditional permission models that focus solely on what actions an identity can perform; Trust Radius measures the potential blast radius if an NHI is compromised.
The Trust Radius encompasses:
- Direct permission scope: What systems and data the NHI can access directly
- Delegation authority scope: What permissions the NHI can grant to others
- Chain-effect potential: How many downstream identities could be affected
Security teams can then establish appropriate controls based on an NHI's Trust Radius rather than just its immediate permission set. This shift focus from point-in-time permissions to the potential cascading impact of a compromise.
Delegation Topology Mapping
Understanding complex delegation relationships requires visibility. Delegation Topology Mapping provides a visual representation of these relationships, making it easier to identify risky patterns and potential attack paths.
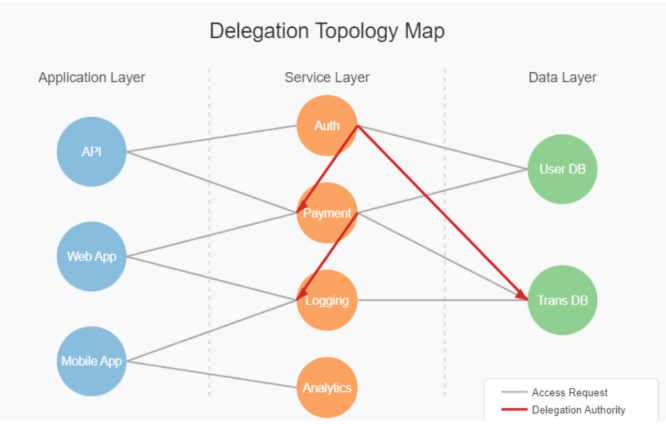
Figure 1: Delegation Topology Map
The diagram above illustrates how delegation relationships span across application, service, and data layers. The red arrows highlight delegation authority pathways where one NHI can provision access for others. These pathways often become the most valuable targets for attackers, as they provide leverage to move laterally and vertically through systems.
Key patterns to identify through topology mapping include:
- Delegation hubs: NHIs that can grant access to numerous other identities
- Cross-layer delegations: Authorization that jumps security boundaries
- Circular delegations: Chains that create loops, potentially enabling privilege escalation
- Orphaned delegations: Authorities that remain after the original business need has disappeared
Practical Implementation Challenges
Implementing effective governance for NHI delegation chains faces several practical challenges:
Visibility Gaps
Traditional identity governance tools excel at managing human users but often provide limited visibility into machine-to-machine delegation. Many security teams struggle to answer basic questions like "Which service accounts can provision temporary access for other service accounts?" or "What's the maximum level of access an attacker could achieve by compromising this application identity?"
Dynamic Environments
Modern cloud-native environments make this challenge even more complex. Auto-scaling, ephemeral resources, and infrastructure-as-code mean NHIs are continuously created and destroyed. Traditional governance approaches that rely on periodic reviews simply can't keep pace.
Cross-Platform Consistency
Most enterprises operate hybrid environments spanning multiple cloud providers and on-premises systems. Each platform implements NHI delegation differently, creating a fragmented governance landscape that attackers can exploit by finding the weakest link.
The Permission Decay Pattern
A promising approach to mitigating these risks is implementing "Permission Decay." This pattern introduces automatic degradation of privileges based on delegation chain length.
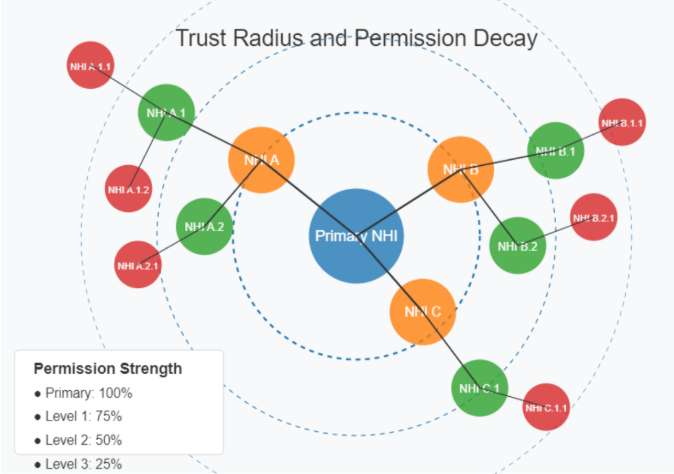
Figure 2: Trust Radius and Permission Decay Visualization
In this model, permissions automatically degrade with each delegation step:
- First-level NHIs receive a set percentage (e.g., 75%) of the original NHI's access scope
- Second-level NHIs receive a further reduced percentage (e.g., 50%)
- Third-level or beyond might be restricted to read-only access (25%)
This approach limits the potential damage from a compromised NHI deep in the delegation chain while aligning with the principle of least privilege. It creates natural security boundaries that contain breaches without requiring constant manual intervention.
Best Practices for Managing NHI Delegation Chains
Based on lessons learned from organizations that have successfully tackled this challenge, several best practices emerge:
- Implement Just-in-Time Access
Replace permanent delegation authorities with just-in-time access requests. When NHI A needs to provision access for NHI B, it makes a time-limited request that automatically expires. This significantly reduces the persistent attack surface.
- Establish Chain Length Limits
Set a maximum delegation chain length based on risk tolerance. For critical systems, consider restricting delegation to a single level to prevent complex chains that are difficult to audit and secure.
- Create Cross-Platform Governance
Develop platform-agnostic policies that define consistent rules for NHI delegation across all environments. These policies should define:
- Which types of NHIs can have delegation authority
- What permissions they can delegate to others
- Maximum chain lengths for different security classifications
- Required monitoring and alerting thresholds
- Implement Autonomous Monitoring
Traditional periodic reviews aren't sufficient for fast-changing NHI relationships. Implement continuous monitoring that can detect:
- New delegation relationships that violate governance policies
- Changes in existing delegation authorities
- Unusual patterns of access requests between NHIs
- Delegation relationships that haven't been utilized recently
The Path Forward: Breaking the Chain Before It Breaks You
The uncomfortable truth about NHI delegation is that most organizations are running on borrowed time. Security teams are drowning in alerts while invisible machine-to-machine trust relationships multiply beneath the surface. When (not if) attackers exploit these chains, the damage can spread far faster than human responders can react.
This isn't just another checkbox on the security roadmap; it's a fundamental shift in how we conceptualize identity security. The old model of "manage each identity individually" collapses under the weight of modern distributed systems, where automation manages automation.
Rather than trying to perfect permissions for thousands of individual NHIs, forward-thinking security teams are tackling the problem at the relationship level. By focusing on the connections between identities rather than just the identities themselves, security teams can identify and mitigate risks that traditional approaches miss entirely.
The three approaches outlined in this article - Trust Radius implementation, Delegation Topology Mapping, and Permission Decay patterns - provide a framework for managing these complex relationships. Each builds upon the others to create a more complete picture of machine identity risk and more effective controls.
As machine identity proliferation accelerates, the organizations that thrive will be those that recognize delegation chains as a distinct security domain requiring specialized governance. The challenge isn't simply technical; it requires rethinking how we conceptualize identity relationships in an increasingly automated world.
The security landscape is shifting from managing what machines can do to understanding what they can empower other machines to do. Organizations that master this transition will find themselves not just more secure but more agile, finally breaking free from the false choice between innovation speed and robust security controls.
@aditya a fascinating article proposing NHI Delegation Chains, including the concept of The Permission Decay Pattern - I have not seen this type of concept presented before and may have real applicability with Agentic AI processes that start interconnecting and talking to each other. I will need more time to digest, would love to hear other folks thoughts.

