Read full article from Felix Gaehtgens here: https://www.linkedin.com/pulse/kubernetes-secrets-critical-examination-felix-gaehtgens-13ipf/?utm_source=nhimg
Key Findings:
- Operational Convenience vs. Security Risks - Kubernetes Secrets simplify sensitive data handling but introduce significant security concerns, including exposure risks and credential rotation difficulties.
- Governance and Accountability - A governance gap exists between teams implementing Kubernetes Secrets and those managing associated risks, causing unmanaged credential proliferation.
- Security Concerns - Kubernetes Secrets lack runtime controls, are challenging to rotate securely, offer limited auditing, and are vulnerable to misconfigurations.
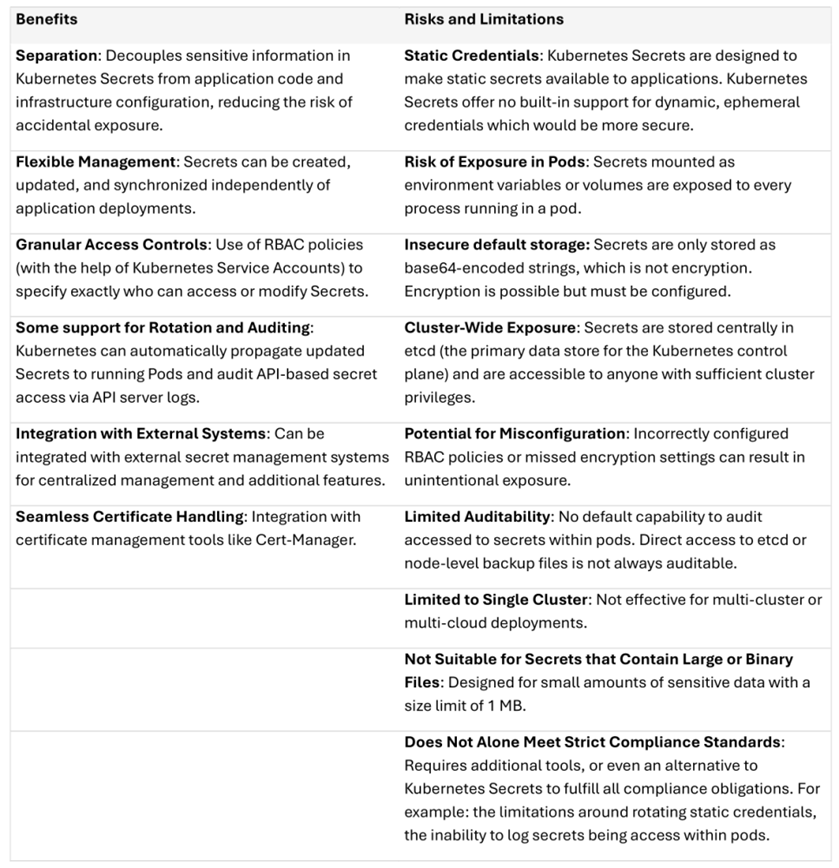
- Benefits and Risks - Despite benefits such as separating secrets from code, Kubernetes Secrets carry risks like static credentials, exposure in pods, insecure default storage, and limited auditability.
- Best Practices - Recommended practices include limiting secret visibility, avoiding secret logging, regularly rotating secrets, implementing RBAC controls, enabling encryption at rest, and using external secret management integrations.
- Alternatives and Combinations - Alternatives such as Kubernetes Service Accounts, secrets management tools, SPIFFE, or combining these methods with Kubernetes Secrets significantly improve security.
Introduction
Kubernetes Secrets provides a simple mechanism to handle sensitive data like API keys and passwords within Kubernetes, but their use introduces risks that IAM leaders and CISOs must consider carefully. Although convenient, Kubernetes Secrets pose significant challenges, including credential sprawl and lack of centralized accountability. This article aims to highlight these challenges, examine integrations with external tools, and provide guidance for securing Kubernetes Secrets or choosing safer alternatives.
Using an analogy of a beautiful yet thorny Bougainvillea, the article emphasizes the hidden complexities and dangers behind the convenience of Kubernetes Secrets.

A key issue with Kubernetes Secrets is the disconnect between teams responsible for their implementation and security teams managing their risks. Often implemented without input from IAM leaders and CISOs, this creates significant governance and security challenges:
- IAM leaders face a governance challenge, as Kubernetes Secrets frequently represent machine identities and static credentials managed by non-IAM teams. Without centralized oversight, organizations risk unmanaged credential sprawl, limited visibility, and compromised lifecycle management, undermining IAM strategies
- CISOs face acute security concerns. Kubernetes Secrets lack granular runtime security controls, secure credential rotation mechanisms, comprehensive auditing capabilities, and are prone to misconfigurations—making them prime targets for attackers. While Kubernetes Secrets support "shift left" initiatives (embedding security early in development), they simultaneously introduce new risks and vulnerabilities
The report also includes a comparative table clearly summarizing the independent benefits and risks associated with Kubernetes Secrets.
What Are Kubernetes Secrets?
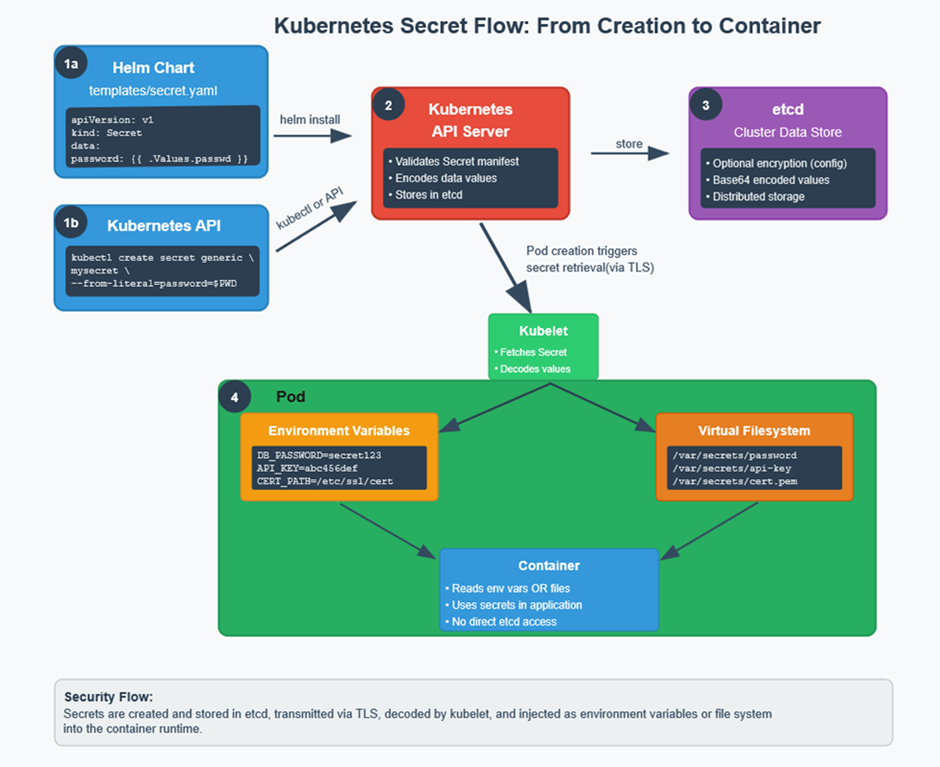
Kubernetes Secrets are specialized Kubernetes objects explicitly designed to securely store and manage sensitive data within Kubernetes clusters, distinctly separated from non-sensitive configurations typically handled by ConfigMaps. They ensure sensitive information is protected from accidental exposure by isolating it from application code, container images, and general configuration files.
Kubernetes Secrets typically contain sensitive items such as:
- Database Credentials (usernames and passwords)
- API Keys
- OAuth Tokens
- SSH Keys
- TLS Certificates and Keys
- Encryption Keys
The Purpose of Kubernetes Secrets
The primary purpose of Kubernetes Secrets is to decouple sensitive information from the application’s code and infrastructure configuration. This separation has several important implications:
- Security - Secrets are not embedded in images or codebases, reducing the risk of accidental exposure via version control systems or container registries
- Flexible Management - Secrets can be created as part of the application deployment (such as Helm charts), or they can be created separately. They can be updated independently of application deployments, facilitating easier rotation and revocation of credentials. Secrets can also be synchronized with other systems, like secrets management tools
- Controlled Access - When combined with Kubernetes Service Accounts, Kubernetes RBAC (Role-Based Access Control) can be used to restrict which users, groups, or service accounts can access or modify Secrets
- Integration - Secrets can be referenced by Pods, making it easy for applications to consume sensitive data without having to store or manage it directly
Advantages of Using Kubernetes Secrets
Kubernetes Secrets offer a convenient alternative to embedding sensitive information in application code or configurations:
- Reduced Risk of Exposure - Stored separately, avoiding leaks via code or configurations
- Encrypted Storage - Supports encryption at rest for secure data persistence
- Granular Access Controls - Integrates with Kubernetes RBAC and Service Accounts to control secret access precisely
- Handling External Credential Changes - Allows updating secrets independently from application deployments, automatically propagating changes to running pods.
- Integration with External Secret Stores - Easily connect with external secret management systems (HashiCorp Vault, AWS Secrets Manager, Azure Key Vault)
- Seamless Certificate Handling - Integrates with tools like Cert-Manager to manage TLS certificates automatically, streamlining lifecycle management
Disadvantages and Risks of Using Kubernetes Secrets
Despite convenience, Kubernetes Secrets carry significant inherent risks:
- Kubernetes Secrets are Static - Primarily designed for static secrets; lacks built-in support for dynamic, frequently rotated credentials
- Risk of Exposure in Pods - Secrets mounted in pods (as files or environment variables) are accessible to all processes with matching permissions
- Base64 Encoding Is Not Encryption - Default storage in base64 encoding offers no real security unless encryption at rest is explicitly configured
- Cluster-Wide Exposure - Stored centrally in etcd, accessible with sufficient privileges, increasing the damage if compromised
- Potential for Misconfiguration - Improper RBAC settings, encryption, or logging can unintentionally expose sensitive data
- Limited Auditability - Difficulty tracking unauthorized direct access to etcd or backups; Kubernetes API logs provide limited visibility
- Limited to Single Cluster - Kubernetes Secrets are cluster-specific, unsuitable for multi-cluster or multi-cloud setups without additional tools
- Not Suitable for Large or Binary Files - Designed for small secrets (1MB), unsuitable for larger or binary files
- Does Not Alone Meet Strict Compliance Standards - Alone, Kubernetes Secrets often don’t meet strict regulatory or compliance standards, requiring supplemental solutions
Good Practices for Using Kubernetes Secrets
When Kubernetes Secrets are your only choice, consider these best practices:
- Limit Secret Visibility - Limit secrets to relevant pods or namespaces; avoid unnecessary cluster-wide secrets
- Avoid Logging Secrets - Ensure applications and monitoring systems never log sensitive information
- Regularly Rotate Secrets - Change secrets frequently, automate rotations if possible, and ensure seamless application updates (though challenging in practice)
- Restrict Access with Kubernetes RBAC - Use service accounts and RBAC policies to strictly control who accesses or modifies secrets
- Enable Encryption at Rest - Encrypt Kubernetes Secrets before storage using Kubernetes encryption features
- Layer with Other Technologies - Combine Kubernetes Secrets with external secret management solutions to enhance security
Alternatives to Using Kubernetes Secrets
Kubernetes Secrets have significant security limitations, especially their static nature. Safer alternatives include:
- Kubernetes Service Accounts - Provides secure workload identities, enforcing authentication, access controls, and auditing within clusters
- Secrets Management Tools - Tools like HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault offer centralized secret management, dynamic credential generation, and enhanced security features
- SPIFFE - Dynamically generates cryptographically secure identities, eliminating static credentials and supporting zero-trust security approaches
Combinations of Using Kubernetes Secrets with Other Methods
Kubernetes Secrets can integrate with other solutions, enhancing security yet adding complexity:
Integration with Secrets Management Tools
External systems (Vault, AWS Secrets Manager, Azure Key Vault) centralize secrets across clusters, simplify management, and enable rotations, but add complexity. Common integration methods:
- External Secrets Operator - Synchronizes external secrets into Kubernetes Secrets
- Secrets Store CSI Driver - Mounts external secrets directly into pods as files or environment variables
Combining Kubernetes Secrets with Kubernetes Service Accounts
Service accounts combined with secrets enforce granular RBAC access controls, enabling detailed auditing and limiting unnecessary secret exposure.
Sealed Secrets
It encrypts Kubernetes Secrets safely in version control. Limitations include manual rotation, dependence on a single private key, and limited runtime security.
Key Management Services (KMS) and HSMs
External encryption (AWS KMS, Google KMS, Azure Key Vault, HSMs) secures secrets stored in etcd, enhancing protection against compromise.
Additional Integration Patterns
- Auditing and Monitoring - Integrate Kubernetes audit logs with monitoring tools, though runtime access is not logged
- Mutating Webhooks - Automatically inject or manage secrets during pod creation
- OPA/Gatekeeper Policies: Enforce custom secret usage policies at pod admission, though not at runtime.
Conclusion Kubernetes Secrets effectively decouple sensitive data from applications, enhancing flexibility and convenience. However, inherent risks—static secrets, exposure in pods, weak default security—must be carefully managed. Employ recommended best practices, integrate with external tools, or use safer alternatives whenever possible. Balance convenience with robust security measures to minimize

