
#1 Authority in NHI Research and Advisory, empowering organizations to tackle the critical risks posed by Non-Human Identities (NHIs).

The only Dynamic Machine Identity Provider for Machines, The Shop Floor, Applications, Services, Workloads, Data Repositories
Website: https://corsha.com

The only Dynamic Machine Identity Provider for Machines, The Shop Floor, Applications, Services, Workloads, Data Repositories
Website: https://corsha.com
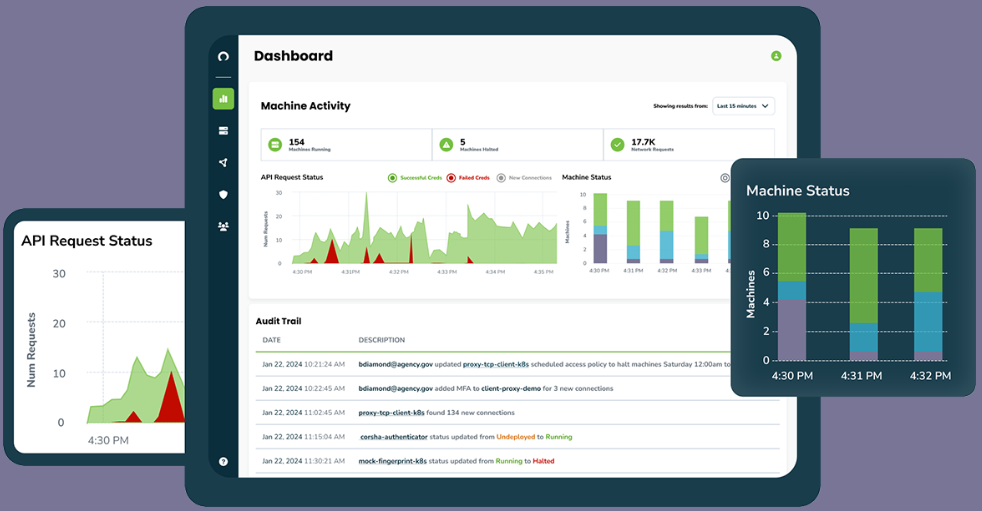
Push past simple secrets and focus on Identity and Access
Dynamic Machine Identities
Discover and Audit Connections
Enforce one-time-use credentials for Machines
Deploy Anywhere
On-Prem
Yes
Cloud
Yes
SaaS
Yes
Account Types
All
Risk Assessment
Yes