In November 2025, security researchers uncovered a widespread supply-chain attack targeting the JavaScript ecosystem. A new malware strain named Shai-Hulud was found infecting over 500 npm packages, silently harvesting sensitive information from developer environments and then exfiltrating secrets to private GitHub repositories controlled by the attackers. The breach highlights once again how fragile the open-source supply chain has become, and how easily compromised packages can escalate into large-scale credential theft.
What Happened?
The malicious campaign revolved around compromised npm packages that developers downloaded and integrated into their projects without knowing they were weaponized. Once installed, the infected packages executed malicious code that harvested:
- API keys
- Environment variables
- Access tokens
- Cloud provider secrets
- GitHub authentication credentials
The stolen data was then transmitted to remote GitHub repositories owned by the attackers.
Because npm packages are widely reused via dependency chains, developers were compromised even if they never installed the malicious package directly, a dependency of a dependency was enough to trigger the infection.
How It Happened
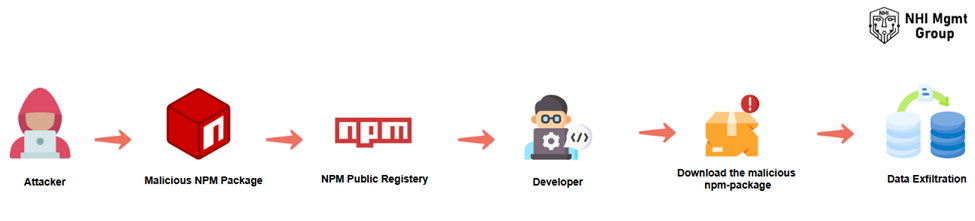
The Shai-Hulud malware infiltrated the npm ecosystem through malicious package uploads that imitated legitimate libraries. Attackers used techniques like:
- Typosquatting – publishing packages with names nearly identical to trusted dependencies
- Dependency hijacking – uploading packages using abandoned or expired namespace names
- Social trust exploitation – inserting malicious updates into previously safe packages
Once downloaded, the malware ran during the package installation lifecycle (via postinstall scripts), enabling it to execute automatically inside developer environments—no manual action required.
From there, Shai-Hulud scanned local machines for secrets commonly used in development workflows and pushed them in bulk to the attackers’ hidden GitHub repositories.
Because the exfiltration traffic blended into normal GitHub API communication, it was extremely difficult for organizations to detect the theft in real time.
What Was Compromised?
The full scope of stolen data is still under investigation, but security research shows that the malware targeted:
- AWS, Azure, and GCP access keys
- GitHub and GitLab personal access tokens
- Environment variables used for CI/CD
- API keys for third-party SaaS platforms
- Database connection strings
- OAuth tokens
Given how many npm packages depend on other libraries, the total exposure could impact thousands of organizations across multiple ecosystems, not just JavaScript projects.
Key Findings by Entro Security
- Banks, Governments, and Fortune 500 companies are affected
- 30,000+ attacker-controlled repos cloned before takedown
- 1,195 organizations identified across tech, finance, government, healthcare
- 55.7% of affected orgs are technology/SaaS companies
- Valid cloud and CI credentials observed up to 72+ hours after disclosure
Key Findings by GitGuardian
- GitGuardian identified 754 distinct npm packages (spanning some 1,700 versions) as infected.
- In their snapshot of 20,649 publicly exposed repositories (as of Nov 24), they found 294,842 “secret occurrences”, corresponding to 33,185 unique secrets.
- Out of those, 3,760 secrets were validated as live/valid at analysis time. Real exposure numbers may have been higher, since some tokens could have been revoked by then.
- Most of the valid secrets were high-value credentials: GitHub Personal Access Tokens (PATs), OAuth tokens, etc.
Possible Impacts
If the stolen secrets are used successfully, organizations may face:
- Unauthorized access to cloud environments
- Source code and intellectual property theft
- CI/CD pipeline compromise
- Lateral movement into internal networks
- Creation of fraudulent infrastructure using real organization credentials
- Downstream customer breaches through trusted integrations
- Ransom, extortion, or data destruction attacks
Recommendations
To reduce risk and respond effectively:
- Rotate all secrets stored in development environments and CI/CD pipelines
- Audit GitHub access tokens and revoke suspicious or unused ones
- Scan source code and repos for embedded secrets using automated tools
- Implement a centralized secrets management solution (e.g., Vault, AWS Secrets Manager, Doppler)
- Enable dependency pinning and dependency integrity checks
- Adopt software composition analysis (SCA) and SBOMs to monitor open-source changes
- Block automatic execution of postinstall scripts unless required
How NHI Mgmt Group Can Help
Incidents like this underscore a critical truth, Non-Human Identities (NHIs) are now at the center of modern cyber risk. OAuth tokens, AWS credentials, service accounts, and AI-driven integrations act as trusted entities inside your environment, yet they’re often the weakest link when it comes to visibility and control.
At NHI Mgmt Group, we specialize in helping organizations understand, secure, and govern their non-human identities across cloud, SaaS, and hybrid environments. Our advisory services are grounded in a risk-based methodology that drives measurable improvements in security, operational alignment, and long-term program sustainability.
We also offer the NHI Foundation Level Training Course, the world’s first structured course dedicated to Non-Human Identity Security. This course gives you the knowledge to detect, prevent, and mitigate NHI risks.
If your organization uses third-party integrations, AI agents, or machine credentials, this training isn’t optional; it’s essential.
Conclusion
The Shai-Hulud attack is another reminder that cybercriminals are increasingly targeting the software supply chain, not enterprise networks directly. Developers and CI/CD environments now represent one of the most valuable attack surfaces because stealing a single set of credentials can unlock access to cloud accounts, infrastructure, and entire customer ecosystems.
Organizations that treat secret management, dependency security, and supply-chain monitoring as optional will remain exposed. Protecting development pipelines, and the NHIs (non-human identities) inside them, is now a core security responsibility, not a nice-to-have.
