User Access Reviews (UARs) are a foundational security practice for enterprises. They reduce business risk and support regulatory compliance by securing access to critical and sensitive resources and data. However, current tools and processes often constrain UARs to a compliance-focused task, thereby limiting their impact as a proactive security control.
Why We Need UARs
UAR is a process to validate that users have the appropriate access to systems, applications, and data – ensuring that it aligns with business needs and job responsibilities.
Given that 93% of enterprises have faced identity attacks in the past two years, and over 95% of identities are found to have excessive privileges, effective UARs are vital to a robust Identity and Access Management (IAM) strategy.
UAR initiatives are typically led by the Governance, Risk, and Compliance (GRC) team. Their primary objectives include removing unnecessary access, meeting compliance rules, and lowering business risk. Despite their inherent value, current tools and processes frequently confine UARs to a compliance exercise, hindering their effectiveness as a proactive security control.
This blog examines the comprehensive UAR process, the challenges organizations encounter, and how to transition towards a more effective, risk-focused approach that also meets compliance requirements. We will examine how context and automation, when enhanced by AI, have the potential to improve the speed and accuracy of UARs, and reduce the operational burden.
How UARs Work
In User Access Reviews (UARs), the GRC team or Asset Owners are responsible for attesting to and proving that users have the correct level of access to designated assets and resources. This validation encompasses applications, cloud infrastructure, role-based access within critical systems, and group memberships.
The initial stage of a UAR campaign is to identify and document all existing user access right and create a comprehensive access inventory. This can be complex, especially in cloud environments where access privileges may not be directly assigned but can be obtained indirectly, such as through lateral movement capabilities like AWS AssumeRole.
Depending on the campaign’s scope and the assets, the review and approval process is typically performed by:
- Users’ managers
- The relevant asset owners
- The security/GRC team
A UAR campaign has a defined duration. During this period, designated reviewers must evaluate each user’s access. They will either approve the continuation of access or recommend its revocation. Once all reviews are complete and the recommended revocations are implemented, the UAR campaign concludes.
Auditors then examine the campaign report and may request detailed information about the review decisions and access revocation process. A thorough audit trail of all process steps and decisions is essential to answer any questions that arise.
Traditional UARs are Tedious and Ineffective
Traditional UARs are often time-consuming, complex and ineffective. Reviewers are typically presented with a long list of user access records, without any context to guide their decisions.
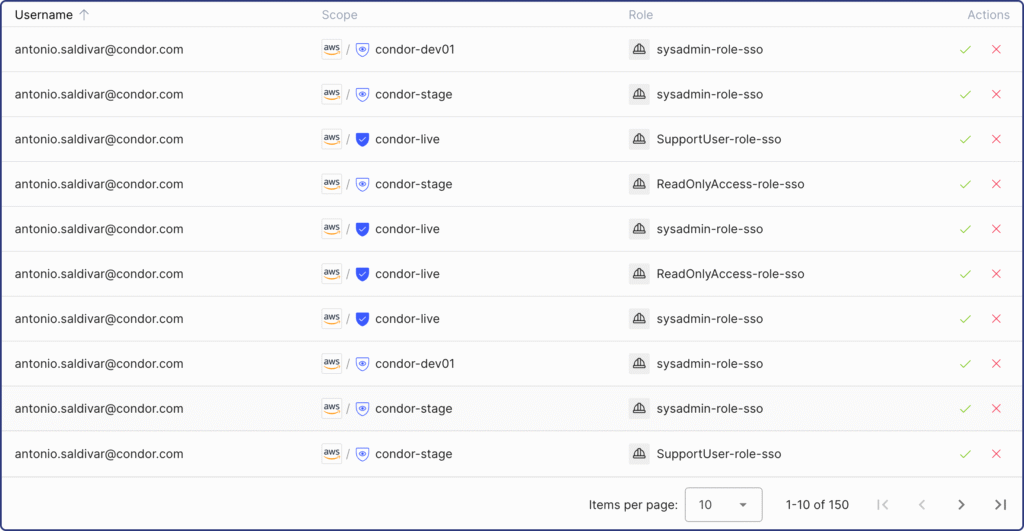
In most cases, there’s very little information about each access being reviewed. For example,
- What is this application used for?
- What capabilities does a role allow?
- What is the implication of a user having this role?
- How and when did they obtain this access?
- Is the access used regularly?
- Is it still needed based on the user’s current role or responsibility?
- What is the potential risk of keeping this access in place?
- Do other team members have similar access, or is it unique to this user?
Access may have been granted for a previous job function, and it’s not always clear whether it should be retained during job transitions or team changes.
Reviewers are faced with time constraints and limited information and they have two options:
- Manually verify every access – a time-intensive endeavor on top of completing their core responsibilities
- Or, say “Yes” to everything
Without understanding what the access does or why it was granted, reviewers risk breaking access to critical applications or disrupt business operations if they revoke it. As a result, they’re not motivated to remove access, and instead approve everything – ultimately defeating the whole purpose of the UAR.
Effective User Access Reviews for Enhanced Security and Efficiency
To transform User Access Reviews into a meaningful security control and reduce administrative burden, organizations must evolve beyond basic workflow tools. The goal is to enable intelligent, context-driven reviews that provide actionable insights and recommendations, allowing the reviewers to make informed decisions about whether to approve or investigate access for potential revocation.
This approach alleviates the manual overhead of traditional UARs, transforming them into an effective initiative for strengthening security and reducing business risk.
An intelligent UAR would automatically assess each user’s access based on relevant factors, mirroring the analysis of an experienced security administrator, including:
- How the user’s access compares to that of their peers in their immediate working group or the larger organization.
- The user’s access usage patterns and recent activity
- Changes in the user’s job title or organizational role.
- The inherent risk level of the access being reviewed
- The overall risk profile of the user.
By analyzing these attributes, a confidence score can be generated to understand which entitlements are:
- Safe to approve,
- Should be flagged for potential revocation,
- Requires further manual review
Imagine a scenario where a reviewer is presented with a more focused list. For instance, if a reviewer needs to evaluate 150 access items across 15 users, an AI model would understand the context of the accesses and provide clear recommendations.
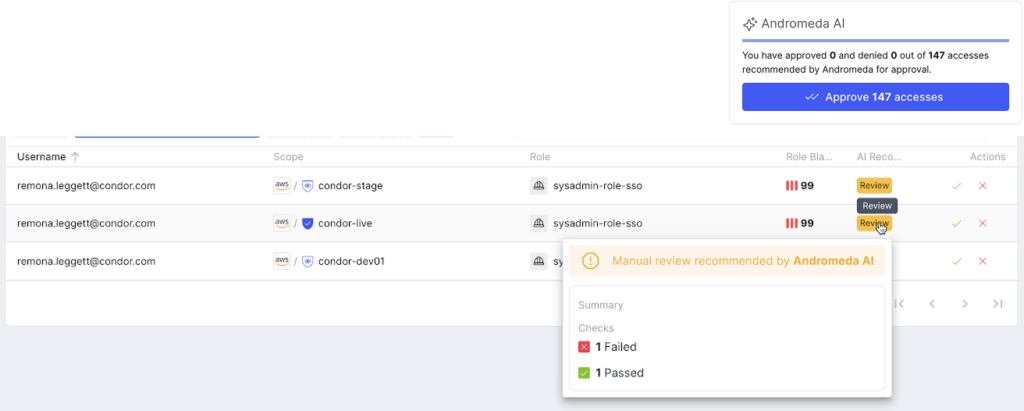
In an ideal world, accesses that require closer review or potential revocation would be accompanied by clear, contextual explanations. These explanations—generated from data analysis and presented in a natural language—would help reviewers understand why an access right is being flagged. With this context readily available, reviewers can make informed decisions without needing to conduct extensive manual investigations.
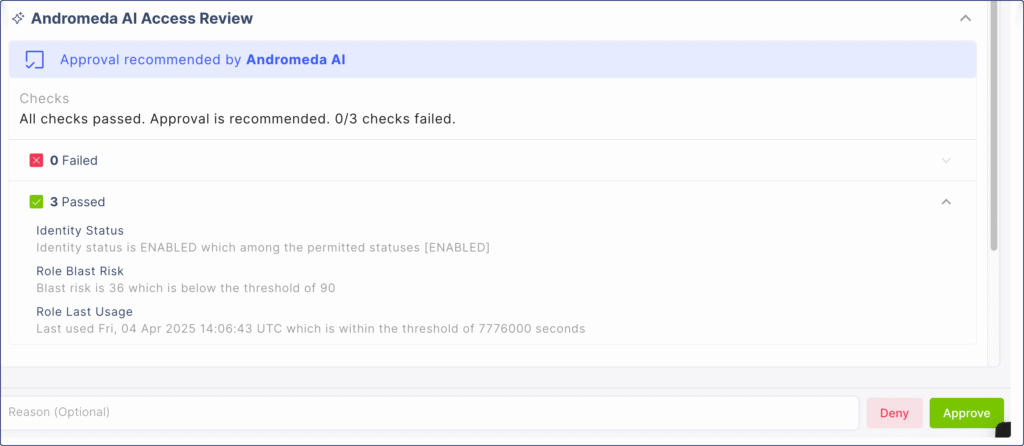
Automated Approval Recommendation with Context
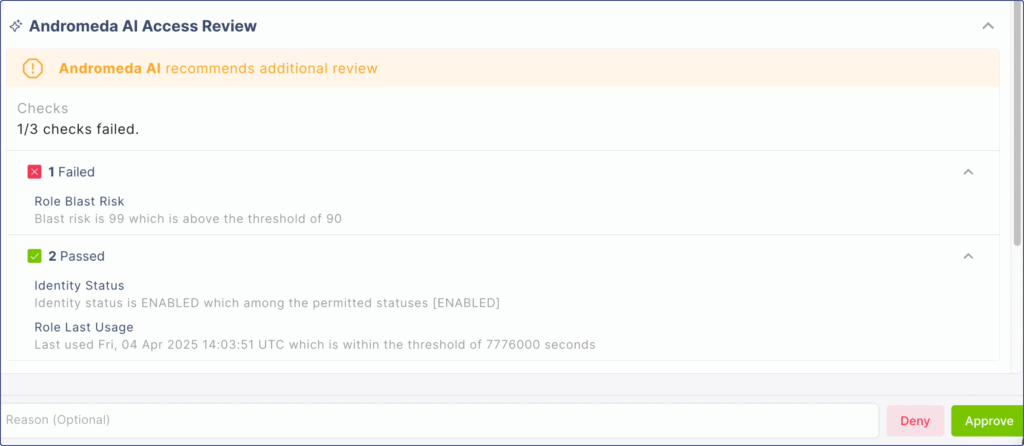
Manual Review Recommendation with Context
The Long-Term Vision: Continuous Compliance
The traditional User Access Review model is misaligned with the realities of today’s dynamic IT environments. It is time to evolve the process to meet modern needs and support a state of continuous compliance. The ideal UAR is an ongoing, intelligence-driven process that adapts to changes in user roles, behaviors, and risk context in real-time. It enables organizations to maintain accurate access controls, reduce the risk of privilege creep, and respond swiftly to emerging threats— while minimizing the operational burden on reviewers.
How Andromeda can help
Andromeda’s security-first User Access Review (UAR) solution enables organizations to easily revoke unnecessary access, meet compliance, and more importantly lower your organization’s risk. Through real-time risk scoring and behavioral insights, Andromeda automates UARs to increase business agility and improve security.
Andromeda Security addresses the most persistent challenges in identity security: excessive and inappropriate access across both human and non-human identities, manual processes and a lack of end-to-end context – compounded by fragmented data. Its data-centric platform unifies identity, entitlement, and activity data into a graph-based architecture—building rich context and laying the foundation for intelligent automation while delivering holistic visibility and remediation. Powered by AI, Andromeda utilizes contextual intelligence built on risk and behavior insights to provide automated and continuous enforcement of least privilege, Just-in-Time (JIT) access, User Access Reviews (UAR), and identity lifecycle governance—helping organizations reduce their attack surface, improve operational agility, and simplify compliance.
