Source – Clutch Security
The Secrets Sprawl Problem
We have a major secrets-sprawl problem in the industry, which has worsened significantly in recent years for several reasons.
Organizations rely heavily on a plethora of interconnected systems and applications, in particular with the adoption and integration of Cloud / SaaS based services. To facilitate seamless interactions and automate processes, they use Non-Human Identities e.g. Service Accounts, Machine Accounts, API keys, and Tokens. However, the widespread and often unmanaged distribution of these credentials can lead to a significant security challenge known as Secrets Sprawl.
This sprawl can lead to various security vulnerabilities, including unauthorized access, data breaches, and compliance issues. What has cause the exponential increase in Non-Human Identities?
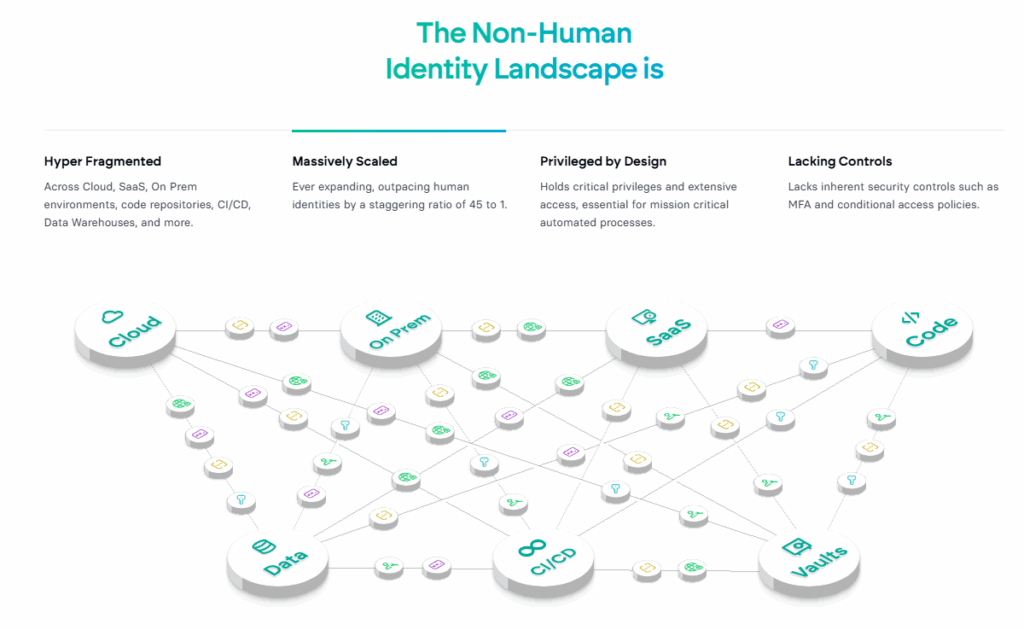
- Hybrid-Cloud Environments
- Cloud-Native Adoption
- Legacy On-Prem Environments
- SaaS Services and associated 3rd Party Supply Chain Risks
- API-Based Service Architecture
- Multiple Identity Providers and Directory Services
- Containerisation and Microservices
- CI/CD Automation and Distribution
- GenAI & LLMs
This has led to hyper-fragmentation, making it very hard to implement controls over this very complex landscape.
- Non-Human Identities outnumber Human Identities by a factor of 25x – 50x.
- Most NHIs are typically static in nature, leading to huge issues and risks that we shared earlier.
- There are multiple identity providers and directory services providers that all have to be factored in across your Hybrid-Cloud and On-Prem environments.
- Particularly with legacy On-Prem environments, NHIs also exist locally on multiple endpoints (e.g., Operating Systems and Databases) that require endpoint connectivity to get visibility, etc.
- You also have to consider all your environments (e.g., Production and Non-Production) as there are issues around the lack of environment segregation, allowing lateral movement.
- A typical organisation has over 300 3rd Party SaaS integrations with limited visibility and a lack of controls on how they are managed internally as well as on the SaaS 3rd Party supplier side.
The Risks of Secrets Sprawl
- Unauthorized Access: When credentials are not properly managed, they can be easily discovered and exploited by malicious actors, both external and internal. This can lead to unauthorized access to sensitive systems and data.
- Data Breaches: Exposed or compromised credentials can result in significant data breaches, causing financial losses, reputational damage, and regulatory penalties.
- Compliance Issues: Many regulatory frameworks, such as SOX, GDPR and HIPAA, require stringent controls over financial or sensitive data. Secrets sprawl can lead to non-compliance and hefty fines.
- Operational Disruptions: Mismanagement of secrets can cause disruptions in automated processes, leading to downtime and reduced productivity e.g. when a credential is cycled, but not all the dependencies are known.
Managing Secrets Sprawl: Best Practices
To mitigate the risks associated with secrets sprawl, organizations should implement robust strategies for managing their credentials.
- Centralized Repository and Ownership: Maintain a single, centralized repository for all secrets to ensure consistent management and monitoring. It is also very important to be ensuring each secret has a defined owner to ensure lifecycle processes are properly managed. Note in reality is very challenging, given the many disparate sources a secret can exist e.g. Directory Services, Cloud/SaaS, Local End Points and in many cases finding an owner can be very challenging.
- Scanning and Secret Management Tools: Use dedicated Scanning tools like GitLeaks and Secrets solutions like HashiCorp Vault, AWS Secrets Manager, or Azure Key Vault to identify hardcoded secrets and then store and manage the secrets securely. Ideally these tools should be integrated/automated into your CI/CD development processes to ensure shift left DevSecOps strategy,
- Principle of Least Privilege: Grant the minimum necessary permissions to service and machine accounts. This limits the potential impact of a compromised credential. Today we see that many secrets are over-privileged and unfortunately shared.
- Automated Secrets Rotation: Regularly rotate credentials to minimize the risk of compromise. Automated tools can help manage the lifecycle of secrets and ensure they are updated without manual intervention. Note this however in practice is very challenging to do, given the various end-points that need to support automated rotation capabilities.
- Short-Lived Tokens: Use short-lived tokens where possible to reduce the window of opportunity for attackers. Implement token expiration and refresh mechanisms to maintain security.
- Activity Logging: Enable logging of all actions related to secret access and management. This provides an audit trail that can help detect and investigate suspicious activities
- Anomaly Detection: Use monitoring tools to detect unusual access patterns or unauthorized attempts to access secrets e.g. connections coming from unknown sources or users.
- Training Programs: Educate employees and developers about the importance of secrets management and the risks associated with secrets sprawl. Provide training on best practices and secure coding techniques.
- Security Policies: Establish and enforce security policies related to the creation, usage, and management of Non-Human Identities e.g. Service Accounts, Machine Accounts, API keys, and Tokens.
Conclusion
Secrets Sprawl poses a significant security risk to modern organizations especially with the adoption of Cloud/SaaS based services, but with the right strategies and tools, it can be effectively managed. By centralizing secrets management, enforcing strict access controls, automating credential rotation, and maintaining rigorous monitoring and auditing practices, businesses can protect their sensitive credentials and mitigate the risk of unauthorized access and data breaches. As the digital landscape continues to evolve, proactive secrets management will be crucial for maintaining robust security postures and ensuring compliance with regulatory requirements.
For further details on how to Manage Non-Human Identity RIsks view our white-paper.
