GitGuardian – The State of Secrets Sprawl 2025 Report
It is not a secret. Hard-coded credentials have long been a primary cause of security incidents in the software world. Yet, with the growing complexity of digital supply chains, secrets sprawl is the Achilles’ heel for organizations of all sizes and security postures.
Overview
As we know, the digital world is now expanding and interconnected at a rate never seen before, secrets sprawl has become a major security risk and threat for applications and infrastructure. API Keys, access tokens, and encryption keys are essential to ensure secure access to software, cloud services, and DevOps process. However, the excessive use of these secrets has ended up with massive exposures, commonly in unsecured or public repositories. This report digs deeply into these vulnerabilities, and the techniques used for detection, prevention, and remediation.
Key Findings on Secrets Exposure in 2024
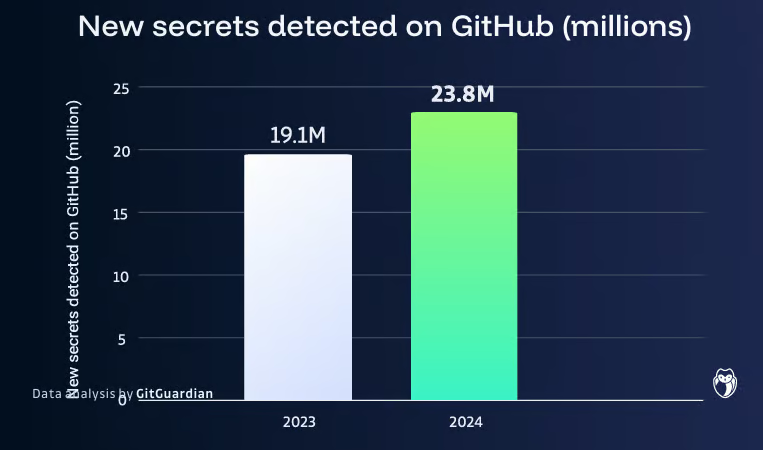
1 – Secrets Exposure in GitHub: GitGuardian has been at the forefront of identifying and reporting hard-coded secrets for the past five years.
- In 2024, 23,770,171 new hardcoded secrets were added to public GitHub repositories, a 25% increase from the previous year.
- The increasing number of secrets and credentials on GitHub is worrying, As GitHub is the most popular platform used by individuals and organizations.
- 58% of all detected secrets were generic secrets, such as hardcoded passwords and database connection strings.
2 – Impact of AI
- AI-enhanced detection has improved the identification and validation of generic secrets.
- GitHub’s Copilot increased the secrets incidence rate by 40%, indicating a need for better security measures alongside productivity tools.
3 – GitHub’s Push Protection
- Although effective for some specific keys, such as OpenAI secrets and GitHub App keys, GitHub’s push protection does not fully address the issue of generic secrets.
4 – Private vs Public Repositories
- Private repositories are 8 times more likely to contain secrets compared to public repositories.
5 – Collaboration Tools
- Collaboration tools like Slack, Jira, and Confluence have a high incidence of secrets exposure, with 38% of incidents classified as highly critical or urgent.
6 – Docker Hub
- Around 100,000 valid secrets were found in public Docker images, emphasizing the need for robust secret management in containerized environments.
Key Stats
- Secrets in Public Repositories:
- 4.6% of all public repositories contain a secret.
- 15% of commit authors leaked a secret.
- 70% of valid secrets detected in public repositories in 2022 remain active today.
- Secrets in Private Repositories:
- 35% of all private repositories contain hardcoded secrets.
- Collaboration Tools:
- 38% of incidents in collaboration and project management tools were classified as highly critical or urgent.
- Docker Hub:
- ENV instructions alone accounted for 65% of all secret leaks.
- ENV instructions alone accounted for 65% of all secret leaks.
