Written by: Jim Curtin, TrustFour
TrustFour’s mission is to give organizations the visibility and tools to protect their networks from unauthorized or adversarial lateral movement thus reducing the blast radius and catastrophic loss related to a credentials breach in the user or Non-Human Identity (NHI) realm.
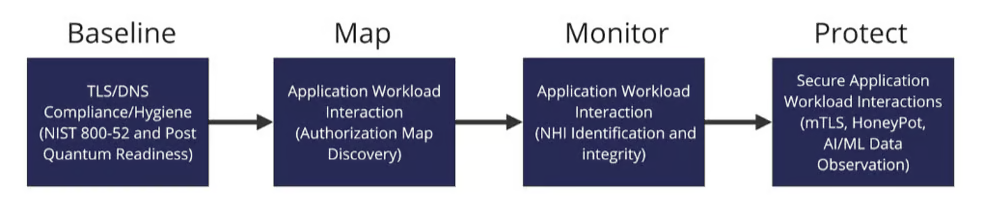
Compliance and hygiene are the building blocks of a strong defense. As Peter Drucker said, “you can’t manage it if you can’t measure it”. T4 starts the journey towards a more secure network infrastructure by scanning the E-W network for TLS compliance against the NIST 800-52 standard, looking at versions, ciphers and 40 other attributes in the standard, including the newly issued Post Quantum Readiness ciphers and recommendations. In addition, the assessment captures all of the DNS information to determine what is duplicated, stale or in-use. Based on this information, we are able to recommend remediation steps to tighten up the compliance and address the exposures and vulnerabilities.
The second phase of our assessment identifies critical servers and services and creates an application-by-application workload connectivity authorization map as well as monitor activity to identify an inventory of all non-human identities and service account credentials interacting in the workload connectivity flow.
At the end of the Assessment Phase, T4 will have proven the value and effectiveness of our”protect” mode which enforces mTLS between each workload dramatically reducing the attack surface while giving visibility and alerts to unauthenticated and unauthorized traffic across the application workload map. This also provides an extra layer of protection to compromised service accounts or Non-Human Identities in the environment.
To ensure proactive improvement and optimized/efficient sustaining of the environment, T4 introduces two streams of valuable telemetry — hacker activity coming from our advanced deterrence elements (honeypots) as well as our ability to observe application data-in-transit. Both streams are fed to advanced AI/ML engines analyzing patterns and vectors to match against other flows as well as recommend actions to streamline to maintenance and functioning of the platform.
Whether you are looking for a snapshot of your network infrastructure compliance and vulnerabilities or embarking on a journey to optimize the resources and effectiveness of your lateral movement detection and deterrence through a shift-left and shift-up capability, T4 is the partner for you. Shift-left, because we allow DevOps and CI/CD organizations to add our infrastructure-as-code as part of their release process (no code changes required), while shifting the responsibility for workload interaction integrity “up” from the network ops and zero trust segmentation teams to the application architects and owners, all while providing common visibility to the alerts, flows, status and telemetry coming out of the T4 platform.
Our assessment roadmap deployment involves 4 phases — Baseline (TLS, DNS), Mapping (authorized connections, inventory of NHIs), Monitoring (full capture time period) and Protect (enforcing mTLS across all workload connections, providing telemetry from honeypots and Data-in-transit observability)
TrustFour’s goal is to reduce adversarial lateral movement, while giving visibility to compliance, hygiene and post-quantum readiness all while reducing the burden on overwhelmed and understaffed security and IT teams.
