In October 2021, Twitch, the popular live streaming platform, suffered a significant data breach, that exposed a significant portion of its internal source code. The incident, which made waves in the cybersecurity world, revealed not only the platform’s source code but also other sensitive data like internal tools and proprietary systems. The leak included 200GB of data, which attackers made public, including credentials, secrets, API keys, and even configuration files. This made it clear that the breach was far more than a simple leak of code; it opened up several security vulnerabilities for exploitation by malicious actors.
What Happened?
The breach took place when an attacker successfully compromised Twitch’s internal systems. The hacker gained access to Twitch’s internal Git repositories and extracted over 200GB of data, including proprietary source code, internal tools, configuration files, and secret keys. The leak was discovered when the attacker released the data publicly on an online forum 4chan, exposing highly sensitive information. Some of the leaked data included internal API keys, client secrets, and a variety of other credentials that could allow malicious actors to further compromise Twitch’s systems.
What Was Leaked?
This massive leak not only gave unauthorized individuals access to Twitch’s source code but also provided them with valuable insights into its inner workings. Importantly, the leak included:
- Total Repositories Exposed: 6,000
- Total Documents Exposed: 3,000,000
- Total Size of Leaked Data: 200GB
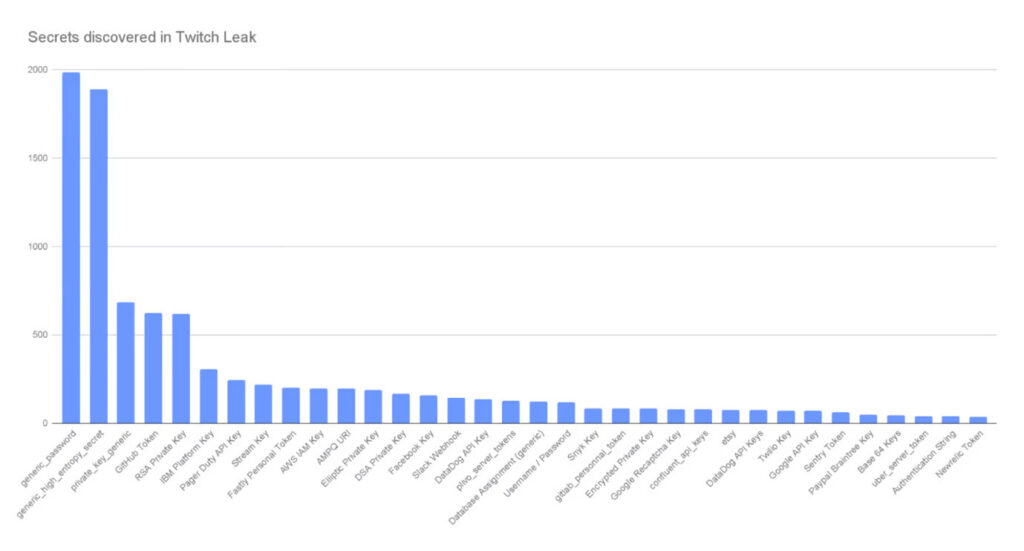
- Secrets Found: Nearly 6,600
- AWS Keys: 194
- Twilio Keys: 69
- Google API Keys: 68
- Database Connection Strings: Hundreds
- GitHub OAuth Keys: 14
- Stripe Keys: 4
How the Breach Occurred
The root cause of the breach was identified as a server configuration error, which allowed unauthorized access to the Twitch servers. This misconfiguration could have involved backup servers or Git servers that were inadvertently made public. While Twitch’s official statement was limited, it indicated that the incident was a result of this improper access.
Potential Impact
Exposing source code publicly can have far-reaching consequences for any company, but especially for those like Twitch that serve millions of users and handle significant amounts of sensitive data. Here are a few key risks that arise when source code is exposed:
- Credential Leaks – When sensitive credentials like API keys, database passwords, or OAuth tokens are exposed, attackers can use them to gain unauthorized access to various systems. Even with encryption in place, a compromised secret key can potentially unlock entire services.
- Vulnerabilities in Code – Exposing source code allows attackers to study it for potential vulnerabilities. With enough time and effort, they can reverse engineering the code, discover unpatched bugs, or find logic flaws in the system that can be exploited. In Twitch’s case, attackers could have identified weaknesses that allowed them to access user data, manipulate streams, or even disrupt services.
- Reputation Damage – Beyond the technical risks, exposing source code can lead to significant damage to a company’s reputation. As seen in past incidents, breaches like these often result in users abandoning the platform, media scrutiny, and a long-term loss of confidence in the company’s security practices.
Lessons Learned
- Audit and Secure Access Controls – Implementing robust access controls and monitoring systems is essential for detecting suspicious activity early. This includes restricting access to sensitive repositories, enforcing multi-factor authentication (MFA), and regularly reviewing permission levels.
- Code Reviews and Static Analysis – Regular code reviews and the use of static code analysis tools can help detect hardcoded secrets, unpatched vulnerabilities, or insecure coding practices before they make it into production.
- Secrets Management – The most crucial takeaway is the importance of never embedding secrets like API keys or passwords directly in source code. Tools like environment variables or secret management should be used to store sensitive data outside of the codebase.
Conclusion
The Twitch leak of 2021 was a stark reminder of the vulnerabilities that can exist in the software development lifecycle, particularly around source code management and secrets handling. For any organization, safeguarding source code and sensitive data should be a top priority to prevent similar breaches.
The lessons learned from this incident are crucial for developers and security professionals in all industries to better secure their systems, protect their users, and maintain trust in their platforms. By implementing best practices for code security, credential management, and incident response, organizations can minimize the risk of future security breaches.
