In September 2024, a security researcher recently demonstrated how a series of flaws in a CI/CD environment resulted in a full server takeover. The attack started with an exposed .git directory, progressed through mismanaged CI/CD pipeline configurations and ended up with unauthorized server access.
Incident Analysis
Root Causes
Public Exposure of the .git Directory
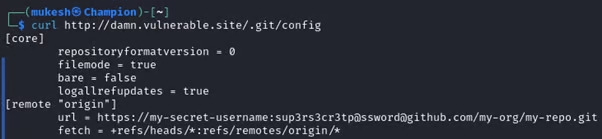
The .git directory, which stores the entire version history of a project, including configuration files which contains sensitive data, was publicly accessible. The researcher exploited this vulnerability to retrieve the repository configuration file and gain access to the credentials.
Weak CI/CD Pipeline Security
The Bitbucket Pipelines configuration stored sensitive information like SSH credentials in plain text and it was configured to log into the production server without any proper security measures.
Attack Technique
Initial Access
Many organizations expose their .git directories by mistake. These directories contain sensitive data and configuration files, in this incident the researcher accessed the .git/config file which contained the repository’s credentials. The researcher used these credentials to clone the repository, giving him the access to sensitive pipeline configurations and scripts.
Bitbucket Pipelines Exploitation
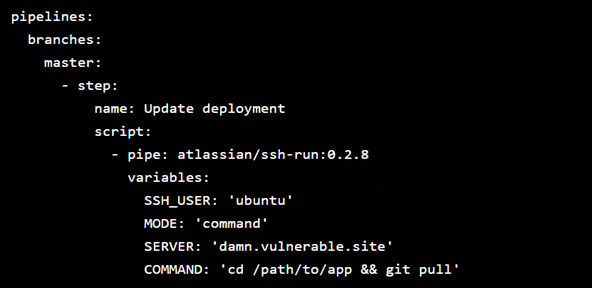
After the researcher successfully cloned the repository with the help of the credentials he found. He discovered that the code owners used Bitbucket Pipelines for automated deployment. The pipeline contained SSH credentials, and it was configured to log into the production server.
Malicious Pipeline Injection
The researcher had the ability to modify the pipeline configuration to execute additional commands. He added his own SSH key to the server’s authorized_keys file using the Atlassian/ssh-run pipe. This change will automatically grant him persistent SSH access.

Unauthorized Server Access
Once the pipeline executed the modified script, the researcher gained SSH to the production server. From there, he could execute any commands and manipulate the server environment.
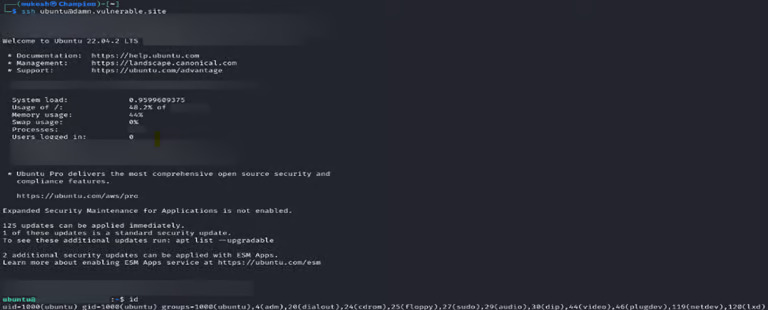
Impact
- Server Compromise: the researcher gained full server takeover with potential access to sensitive data.
- Persistent Backdoor: The SSH key embedded in the new script can provide ongoing access.
Recommendations
Secure .git Directories
- Block public access to .git directories
- Use tools to scan and identify exposed directories.
Harden CI/CD Pipelines
- Regularly audit pipeline configurations for possible sensitive information exposure.
- Restrict access to pipeline tools and enforce role-based access controls (RBAC).
Manage Keys Effectively
- Rotate and revoke unused or outdated keys.
Vulnerability Assessment
- Conduct regular vulnerability scans and penetration tests.
Conclusion
This incident showed us the importance of securing CI/CD environments. Exposed .git directories, improper SSH key management, and poorly configured pipelines presents significant risks. By implementing effective security measures, organizations can avoid these risks and protect their systems from any possible attacks.
