In February 2025, Cisco Talos reported that the advanced persistent threat (APT) group known as Salt Typhoon, believed to be linked to China’s Ministry of State Security (MSS) or Guoanbu, managed to infiltrate several U.S. telecommunications networks. Shockingly, some of these intrusions went unnoticed for more than three years. The attackers took advantage of an old but still unpatched vulnerability in Cisco’s Smart Install feature, known as CVE-2018-0171, while also leveraging stolen credentials to deepen their access. Their approach combined stealth and persistence, making detection incredibly difficult until significant damage had already been done.
Background on Salt Typhoon
Salt Typhoon is a highly skilled cyber-espionage group believed to be backed by the Chinese government. Known for their calculated and methodical approach, they invest significant resources into long-term infiltration of targeted networks. Their primary goal is intelligence gathering, with a strong focus on monitoring communications, conducting counterintelligence operations, and extracting sensitive data, particularly from critical infrastructure like telecommunications. Their ability to remain undetected for extended periods makes them a formidable threat in the cybersecurity landscape.
Vulnerability Exploited: CVE-2018-0171
CVE-2018-0171 is a critical vulnerability within Cisco’s Smart Install (SMI) feature, which facilitates the deployment of new switches. The flaw arises from improper validation of packet data, enabling an unauthenticated, remote attacker to trigger a stack-based buffer overflow. Successful exploitation allows the execution of arbitrary code on the affected device, granting the attacker control over the system. Despite the availability of patches since 2018, Salt Typhoon capitalized on unpatched systems within U.S. telecom networks to gain access.
Attack Methodology
- Initial Access – Salt Typhoon primarily entered targeted networks through two avenues:
- Use of Stolen Credentials – Salt Typhoon obtained legitimate login credentials to access targeted systems. The exact methods of credential acquisition remain undetermined; however, the group demonstrated capabilities to capture SNMP, TACACS, and RADIUS traffic, including secret keys, to enumerate additional credentials.
- Exploitation of CVE-2018-0171 – The Attacker leveraged this vulnerability to gain unauthorized access to Cisco devices. The exploitation allowed the attackers to execute arbitrary code, facilitating deeper penetration into the network infrastructure. Notably, no new Cisco vulnerabilities were identified during this campaign.
- Establishing Persistence – Post-compromise, Salt Typhoon employed several techniques to maintain long-term access:
- Creation of Local Accounts – They generated new user accounts with elevated privileges on compromised devices.
- Enabling Guest Shell Access – This provided a Linux-based container within IOS XE, allowing the execution of scripts and utilities directly on the device.
- SSH Configuration – Modifications were made to permit remote SSH access, facilitating control over the devices from external locations.
- Configuration Exfiltration – Salt Typhoon exfiltrated device configurations using protocols such as TFTP and FTP. These configurations often contained sensitive authentication materials, including SNMP Read/Write community strings and local accounts with weak password encryption types.
- Lateral Movement and Data Exfiltration – To traverse networks and extract data, the group utilized:
Living-off-the-Land (LOTL) Techniques – By leveraging existing tools and commands within the network environment, they minimized the likelihood of detection.JumbledPath Utility – A custom-developed Go-based ELF binary, JumbledPath enabled packet capture on remote Cisco devices via an attacker-defined jump host. It also possessed capabilities to clear logs and disable logging, obscuring malicious activities.
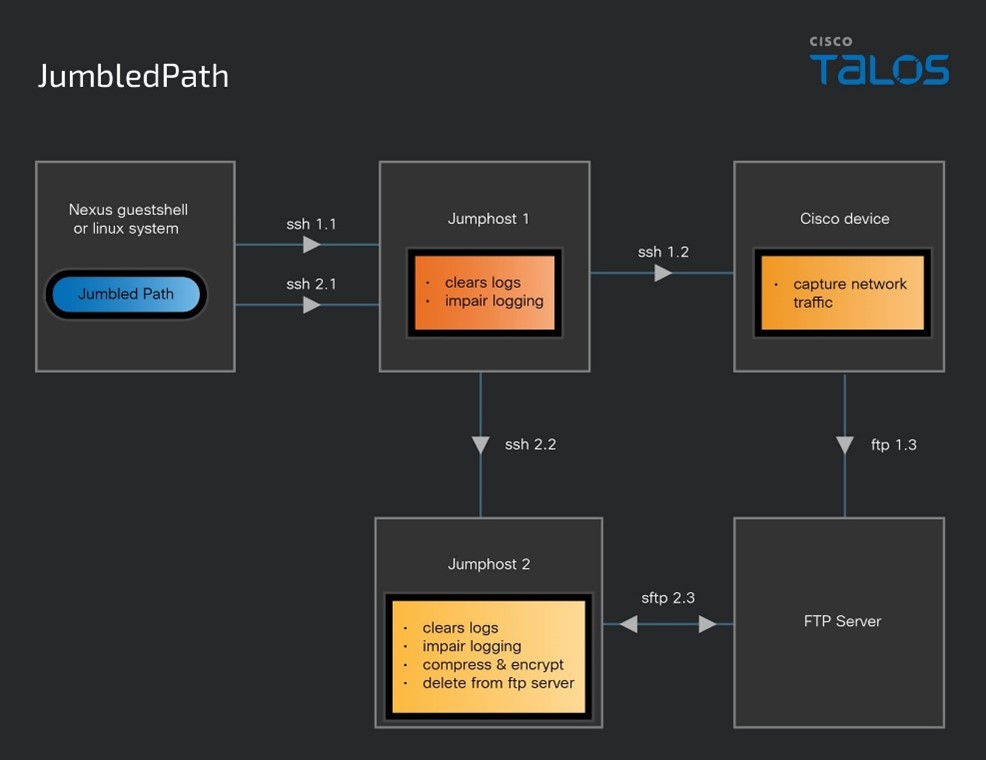
Impact Assessment
Data Exfiltration – Access to sensitive metadata, including call logs and text message details, was achieved, potentially compromising the privacy of millions of users.
National Security Risks – The interception of communications involving high-profile individuals posed significant counterintelligence threats.
Operational Disruption – The unauthorized access and potential manipulation of core network components threatened the integrity and reliability of telecommunications services.
Recommendations
- Data Encryption – Ensure that all sensitive data is encrypted during transmission and while stored.
- Network Segmentation – Divide networks into segments to ensure that even if one segment is compromised, lateral movement across the organization is limited.
- Zero-Trust Architecture – Adopt a zero-trust security model where every access request is verified, irrespective of its origin within the network.
- Vulnerability Scanning – Implement automated tools to regularly scan systems for known vulnerabilities, such as CVE-2018-0171.
- Regular Secrets Rotation – Use an automated secrets manager to rotate your secrets periodically to avoid any data breaches or leaks.
- Regularly Apply Patches – Implement a strict patch management policy to ensure all critical vulnerabilities are patched in a timely manner.
- Anomaly Detection – Implement machine learning and behavior analytics tools to detect deviations from normal system activities, which may indicate lateral movement or other malicious actions.
Conclusion
The Salt Typhoon intrusion into U.S. telecommunications networks underscores the critical need for proactive cybersecurity measures. The exploitation of a known vulnerability, combined with the use of stolen credentials, facilitated a prolonged and damaging breach. Organizations must prioritize the implementation of robust security protocols, regular system updates, and continuous network monitoring to safeguard against such sophisticated threats.
