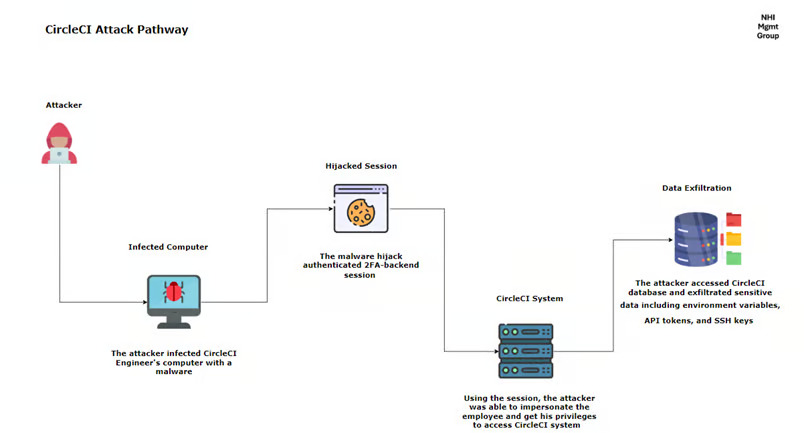
CircleCI, which is considered as a leading continuous integration and delivery (CI/CD) platform, fell victim to a major security breach in Jan 2023. The compromise was facilitated by malware installed on a CircleCi engineer’s laptop, which stole a session cookie authenticated via two-factor authentication (2FA). This allowed the attacker to bypass additional authentication and impersonate the engineer to access internal CircleCI systems. The breach was detected when CircleCI was alerted to suspicious GitHub OAuth activity by one of their customers.
What Happened?
- Initial Access (December 16, 2022) – A CircleCI engineer’s laptop was infected with malware, which successfully bypassed antivirus defenses. This malware stole a 2FA-backend session which enabled the attacker to impersonate the employee. The targeted employee had privileges to generate production access tokens.
- Data Exfiltration (December 19-22, 2022) – The attacker made a reconnaissance to know more about the data that he could steal. Once he figured it out, he used the employee’s high privileges and accessed CircleCI’s databases and exfiltrated sensitive data such as customer environment variables, tokens, and encryption keys. Although the data was encrypted at rest, the attacker also extracted encryption keys from a running process, enabling him to potentially access the encrypted data.
- Detection (December 29, 2022) – The breach was detected when CircleCI was alerted to suspicious GitHub OAuth activity by one of their customers. This activity led CircleCI to investigate further and discover the scope of the breach
- Public Disclosure (January 4, 2023) – CircleCI publicly disclosed the breach, urging all customers to rotate their secrets immediately. The company also invalidated compromised tokens and worked with third-party cybersecurity experts to assist them in the investigation and to validate their findings.
Impact of the Breach
Exposed Customer Data:
- Secrets such as environment variables, API tokens, and SSH keys were exfiltrated.
- Integration credentials for platforms like GitHub and AWS were compromised.
- Although customer data was encrypted at rest, access to encryption keys rendered the protection ineffective.
Operational Fallout
- Customers were forced to rotate all secrets and audit their systems for unauthorized activity.
- Development pipelines relying on CircleCI were temporarily disrupted as tokens were invalidated and rotated.
CircleCI Response
CircleCI took swift action to address the breach and improve its security posture:
Immediate Measures:
- Invalidated all customer secrets stored on the platform.
- Issued guidance for rotating API tokens, OAuth keys, and other secrets.
- Partnered with third-party platforms like GitHub and AWS to automate token rotations.
Enhanced Security Protocols:
- Improved malware detection and blocking mechanisms.
- Introduced step-up authentication measures for privileged access.
- Deployed advanced behavioral monitoring to detect and block suspicious activity.
Customer Support:
- Developed tools to assist with secret rotation and auditing.
- Provided detailed reports and ongoing updates to customers via blogs, emails, and forums.
Lessons Learned
The CircleCI breach highlights vulnerabilities in the security of session cookies and the risks associated with storing sensitive tokens in centralized systems. Key takeaways include:
- Proactive Defenses – Organizations must enforce stricter controls on privileged access, including limiting token lifespan and implementing IP-based restrictions.
- Comprehensive Monitoring – Continuous monitoring for anomalies in token usage and employing automated tools to identify misconfigurations can help prevent similar incidents.
- Zero Trust Architecture – Restricting production environment access and implementing principle-of-least-privilege policies reduce the attack surface.
Recommendations
- Token Rotation – Customers should immediately rotate all secrets stored in CircleCI, including third-party integrations like AWS, GitHub, and Kubernetes.
- Audit Logs – Review recent activity in connected cloud platforms for unauthorized access or suspicious activity.
- Limited Token Scope – Use scoped tokens with minimal permissions to reduce potential damage from token compromise.
- Implement MFA Solutions – Solutions such as MFA number matching can provide stronger security.
- Advanced Malware Detection – Equip employee endpoints with next-generation antivirus solutions and Endpoint Detection and Response (EDR) tools capable of identifying malicious behaviors, such as unauthorized session cookie access or process injection.
Conclusion
The CircleCI breach is a clear reminder of how a single weak point, like a compromised computer or stolen session token, can lead to widespread security issues. It shows how interconnected systems can be vulnerable, with a breach in one platform potentially affecting many others. While CircleCI acted quickly to fix the issue, the incident highlights the limits of fixing problems after they happen and emphasizes the importance of having strong, proactive security measures in place to prevent attacks.
