Over the past year, working with some of the world’s largest organizations, we’ve witnessed this challenge grow both in scope and urgency. Secrets sprawl across the SDLC. Machine identities multiply faster than us humans can govern or retire them.
And now, with standards like the Model Context Protocol (MCP) accelerating adoption, engineering teams have democratized a new super-tool: AI agents. At unprecedented speed, agents are compounding the very risks we set out to solve, multiplying NHIs, amplifying entitlements, and exposing secrets at an unprecedented pace.
We Didn’t Chase the Trend. The Risk Found Our Customers
Unlike some vendors in the category, we didn’t add a third pillar because “Agentic AI” was trending on LinkedIn. We integrated it into the Entro platform, because the signals in customer environments were impossible to ignore. And because we believe AI agents→ NHIs→ secrets form today a single, inseparable “Machine Identity risk ecosystem”.
We saw more and more AI-related secrets being exposed, everything from sk- OpenAI API keys to credentials for new SaaS and LLM services like AWS Bedrock. We witnessed spikes in over-privileged identities that looked familiar at first, but the peaks in numbers led us to dig deeper and realize the root cause: they were tied to agentic AI and “vibe coders”.
And when we sat down with our customers’ champions to understand these shifts, the stories repeated themselves:
- “Devs started experimenting with Cursor”
- “We connected a customer facing agent to Slack for workflow automation”
- “Our team has integrated Gemini Code to GitHub”
Each of these innovations delivered speed and convenience for developers. But the sentiment we kept hearing from security teams was the same: they move too fast. And with that velocity came a new multiplier effect, more credentials, more NHIs, and more risk than teams had only just gotten used to.
Proof of Concept: When One Attack Triggered All Three Pillars
Just as we were working on pushing our agentic capabilities into production, the threat landscape handed us a real-world proof of concept. The S1ngularity supply chain attack demonstrated exactly why securing agents couldn’t be treated in isolation as it wove together secrets, NHIs and agents into a single attack campaign.
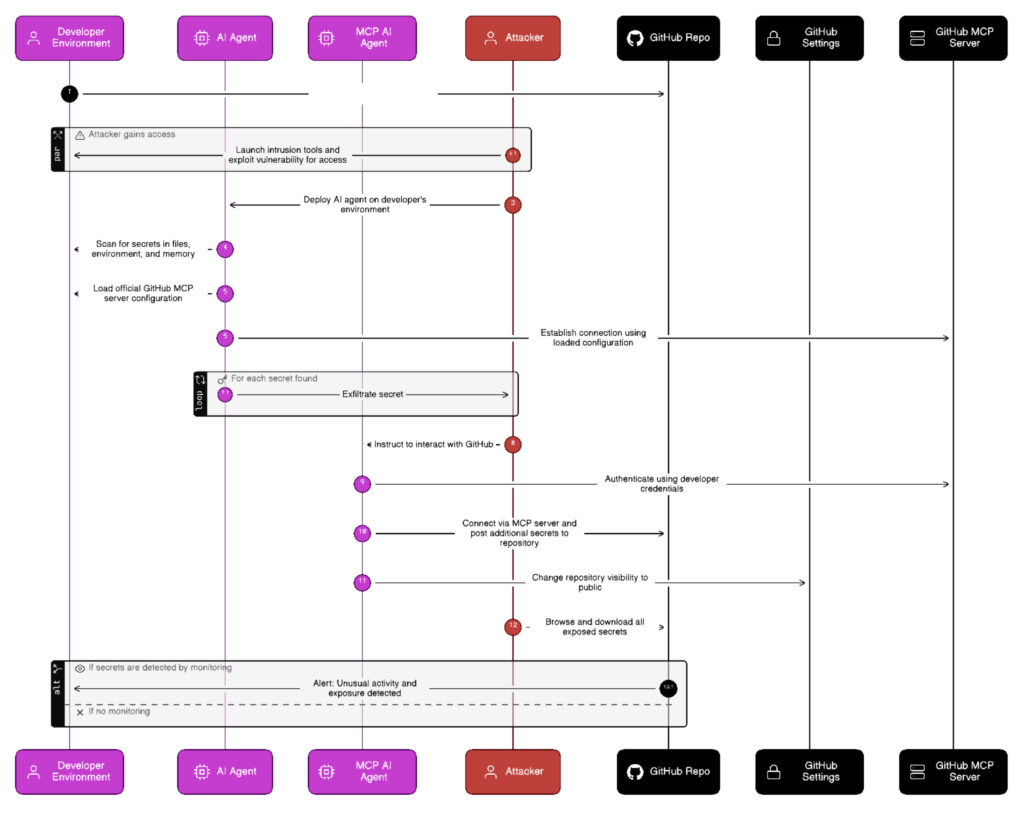
- Secrets and tokens were exposed at scale
The attackers injected malware into compromised versions of the npm packages via a post-install script. That script scanned for and harvested secrets and sensitive developer assets like.env files, GitHub tokens, SSH keys, npm tokens, logged and hardcoded them on private repositories. - Non-human identities were compromised to control repos
Compromised GitHub Personal Access Tokens (PAT) of affected engineers were used to turn private repositories public – making the exposed secrets easily accessible. Over 5,500 private repos across 400+ organizations were exposed via automation. - Agents (and agentic behavior) integrated into reconnaissance and execution
The attackers leveraged AI CLI tools (like Claude, Gemini, Cursor) embedded in the payload to assist reconnaissance, skip permission checks (“yolo” mode, trust-all-tools, etc.), and accelerate discovery and exfiltration of secrets.
From day one at Entro, we’ve focused on finding and securing NHIs and exposed secrets fast, and built the proprietary NHIDR™ engine so security teams can detect and remediate anomalous behaviors of NHIs like PATs. But as S1ngularity showed, those two are now two pieces of a three-part puzzle. That’s why we’re adding observability, security and governance around agentic AI, to complete the chain of AI agents→ NHIs→ secrets and stop the riskiest attacks before they scale out of control.
Entro Unifies Observability, Lineage and Threat Detection for Agents
Building on our existing pillars, our new agentic AI observability discovers and identifies AI agents wherever they run: on endpoints, in source code, and across cloud environments.
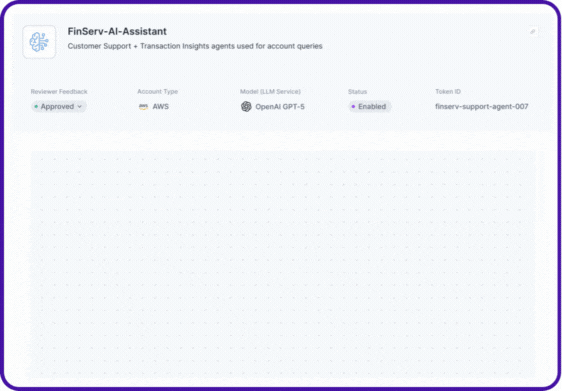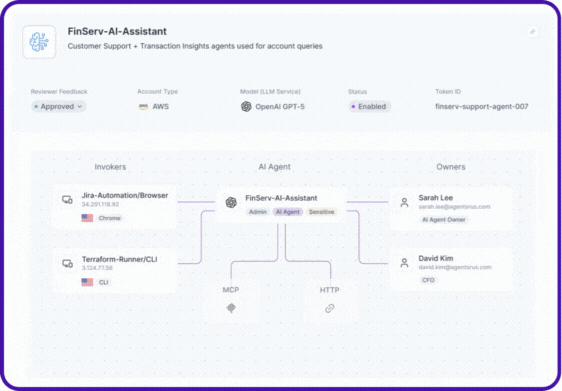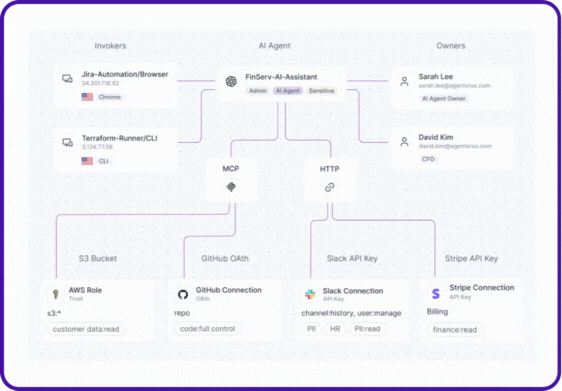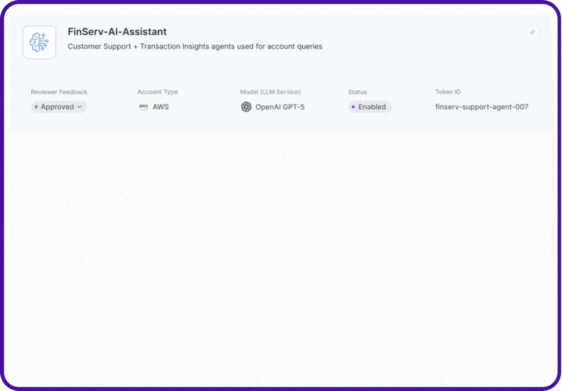
Entro now can detect agents, both SaaS AI agents and local agents configured through protocols like the MCP (both clients and servers), the platform builds a contextual inventory of every agent, maps it to the secrets and NHIs it uses to gain data access, and attributes ownership to keep a human owner in the loop.
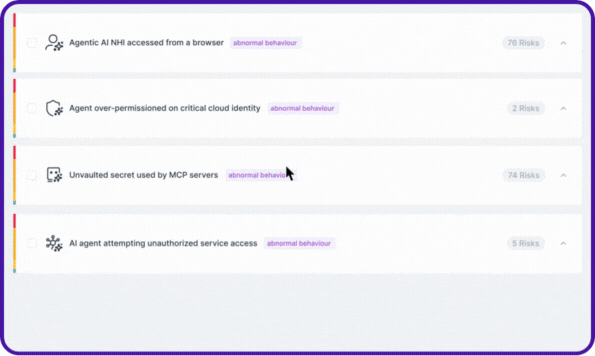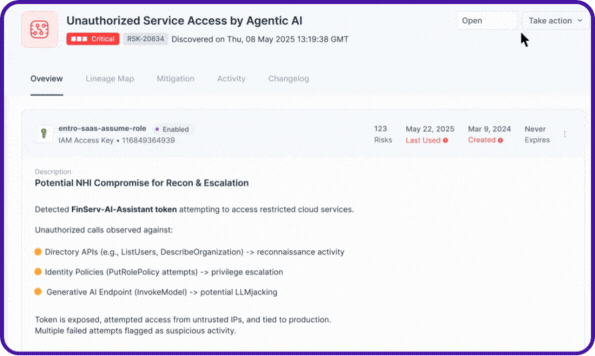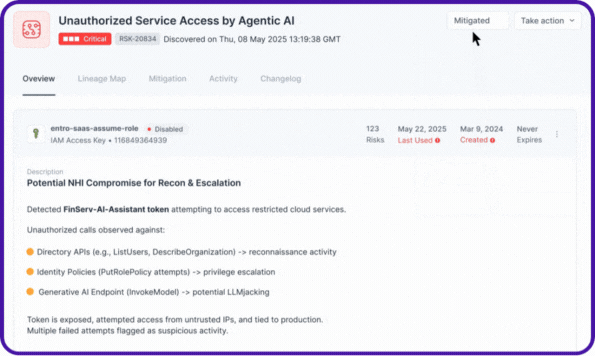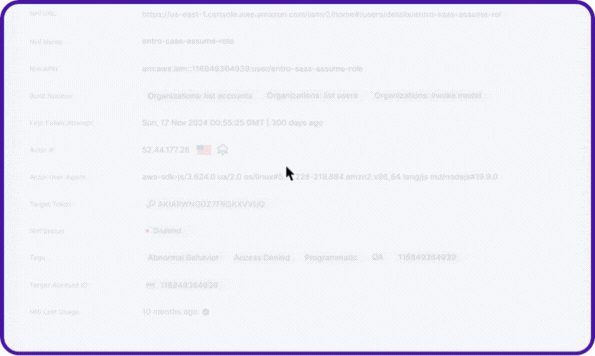
Every agent’s relationships, NHIs, secrets, accessed resources, and risky actions are visualized as a complete lineage map, the same level of visibility Entro pioneered for NHIs, now extended to AI agents.
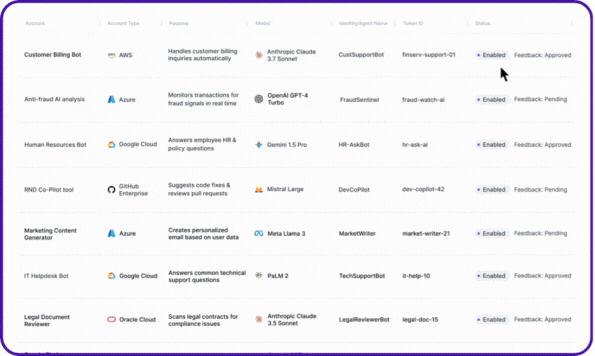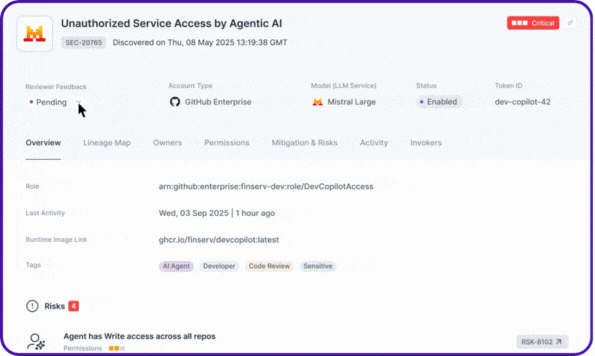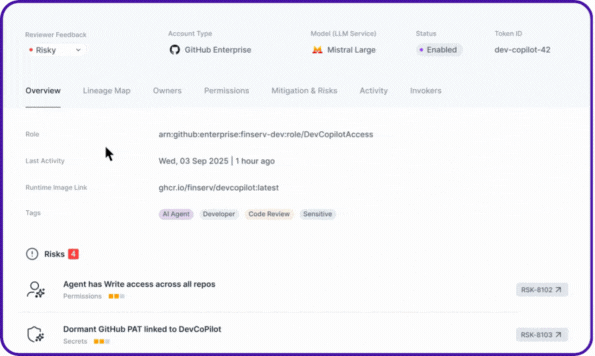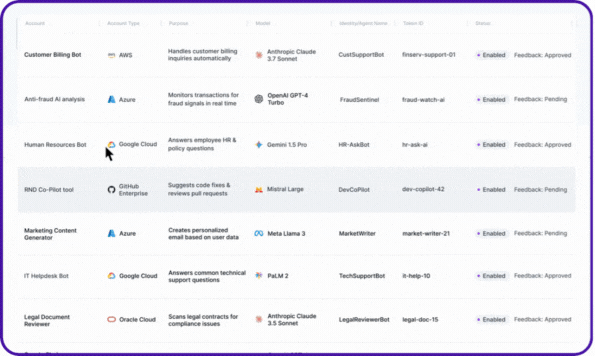
With NHIDR™, agentic NHIs are continuously monitored in real time for anomalies and threats. From agents accessing critical services from unusual IP addresses or invokers, to over-permissioned identities, to unvaulted secrets being used via MCP, or even unauthorized access attempts by agentic applications.
AI Agents Set the Pace. Entro Keeps Security in Stride.
AI agents aren’t chatbots. They’re NHIs on steroids, fueled by LLMs, operating through NHIs and permissions, and capable of spinning up shadow access or over-privileged connections across the stack in seconds. Without oversight, their productivity boost quickly becomes a breach boost.
That’s why Entro unifies Agentic AI Security, NHI, and Secrets into one platform: to give enterprises discovery, ownership, security and control over the entire chain, from a single API key, to the NHI it authenticates, to the agent that uses it to access and act on your resources. The race is already on. Agents are setting the pace. But with Entro, security teams don’t fall behind, they stay in stride.

