Even the users without Dropbox Sign accounts but involved in signed transactions had their In April 2024, Dropbox Sign, a document management and e-signature platform acquired by Dropbox, experienced a significant security breach. Attackers exploited compromised backend service account which granted them the ability to access the customers database which led to the exposure of sensitive user data, including email addresses, usernames, hashed passwords, and account authentication details like API keys and OAuth tokens.information exposed, including email addresses and names.
What went wrong?
Dropbox Sign was targeted through a compromised backend service account, which worked as an automated configuration tool with elevated privileges. This allowed the attacker to access the customers database which contains sensitive information.
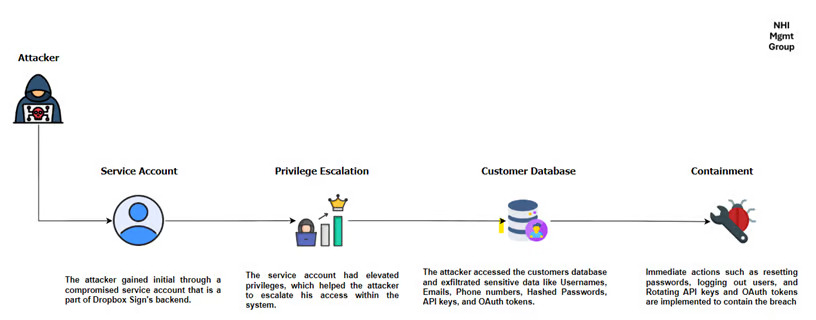
This breach includes:
Exposed Data
- Names and email addresses of the customers, even those who interacted with Dropbox Sign without creating an account.
- While no documents or financial information were exposed, this information could still lead to phishing and identity theft.
Scope
- Only Dropbox Sign was compromised, other Dropbox products were unaffected. This highlights the segmented nature of Dropbox infrastructure, which is an important containment strategy.
Who was Affected?
The breach affected both regular users and organizations that rely on Dropbox Sign for document management. Affected parties could face risks of identity theft, targeted phishing campaigns, and fraud. The breach’s impact is serious since the exposed API keys and authentication information may allow attackers to compromise linked systems, escalating the threat beyond Dropbox’s infrastructure.
Dropbox’s Response and User Recommendations
In response to the breach, Dropbox took several steps:
- Password Resets: All affected passwords were reset, and users were logged out of their accounts.
- Token Revocation: API keys and OAuth tokens were rotated to limit any further unauthorized access.
- Incident Investigation: Dropbox collaborated with third-party cybersecurity firms, law enforcement, and regulators to investigate the breach.
What Users Should Do:
- Change passwords immediately and avoid reusing them across platforms.
- Developers using Dropbox Sign integrations should generate new API keys.
- Add multi-factor authentication to accounts to add an additional layer of security.
Lessons for the Future
This incident highlights the necessity of efficient cybersecurity measures such as:
- Conduct Regular Secrets Rotation: Use an automated secret manager to rotate your secrets periodically to avoid any data breaches or leaks.
- Access Control List: set up access control lists and whitelist the trusted IP ranges to restrict any possible malicious connections with NHIs.
- Role-Based Access Control (RBAC): It’s a security mechanism used to give essential and minimum permissions to NHIs necessary for their role or task to avoid any excessive permissions.
- Implement Zero Trust: Zero Trust security is a security model that requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are sitting within or outside of the network perimeter.
Conclusion
The Dropbox Sign incident highlights the risks of compromised service accounts and the importance of robust security measures. Even though the impact was limited, it shows how important it is for organizations to prioritize user protection, continuous monitoring, and strong access controls to prevent future incidents.
