In June 2024, GitHub users fell victim to an extortion campaign targeting their repositories. The threat actor gained unauthorized access to GitHub accounts using stolen credentials that seemed to be acquired from previous breaches. The attacker deleted the repository contents and replaced them with a README file. Inside the file there are instructions directing the victims to contact the threat actor through Telegram to get their deleted data in exchange for a ransom.
Incident Analysis
Root Causes
Credential Mismanagement
Many users used weak passwords or reused credentials across different platforms, making them more vulnerable to attacks.
Lack of Layered Security
Many compromised GitHub accounts did not have MFA enabled, making it easy for the attacker to access the account by using the password only.
Lack of Monitoring and Detection
Insufficient monitoring of repository activity logs and accounts permissions delayed the detection process of the attack.
Attack Techniques
Initial Access
- The attackers used stolen GitHub credentials obtained from previous data breaches or phishing campaigns.
- The attackers used Malicious OAuth apps to bypass security defences, exploiting users’ trust in third party integrations.
Repository Manipulation
Once the attackers gain access to the users’ repositories, they:
- Deleted all repository contents.
- Renamed the repositories.
- Repository contents were backed up by the attackers to use them for extortion.
Extortion
The attackers replaced the repos with a README file holding a message stating that the data has been backed up and providing instructions to contact the attackers on Telegram and the victims must pay a ransom to get their data back.
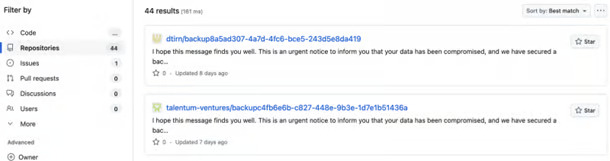
Motivations Behind the Attack
The main motive behind this attack is financial gain through extortion. By deleting repositories content, the attacker caused operational problems and forced the organizations to pay the ransom to get the data back.
Impact of the Attack
Financial Loss
Victims must deal with ransom demands with no guarantee of data recovery even if payment is made.
Workflow Disruption
The deleted repositories will disrupt workflows and could expose organizations to significant delays.
Reputational Damage
The affected organizations may lose the confidence of their customers and partners if the sensitive data is leaked.
Supply Chain Attack Risks
If the affected repositories include dependencies or shared libraries used by other projects or third parties, this could lead to supply chain attacks.
Recommendations
Enable Multi-Factor Authentication (MFA)
All users should enable MFA to add an extra layer of security.
Continuous Monitoring
Regularly monitor and review account activity logs for any unauthorized access or changes.
Secrets Management
Regularly rotate secrets and use strong, unique passwords for each account.
Review Authorized Apps
Review and audit all OAuth apps and revoke access to any suspicious ones.
