In September 2022, Microsoft disabled compromised verified partner accounts exploited by attackers to conduct OAuth phishing campaigns. These campaigns utilized rogue OAuth applications to deceive victims into granting attackers unauthorized access to sensitive data, such as email, files, and cloud resources within Microsoft 365 accounts. This sophisticated attack highlights the evolving nature of phishing threats, particularly those exploiting third-party application integrations.
What is OAuth Phishing?
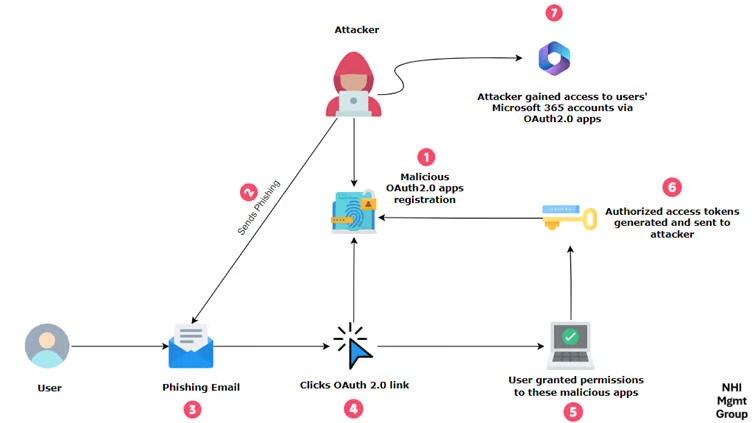
OAuth phishing, also known as consent phishing, manipulates the OAuth 2.0 protocol. Instead of stealing login credentials, attackers deceive users into granting permissions to malicious applications registered on cloud platforms like Microsoft Azure. Once access is granted, attackers can use the obtained tokens to access user accounts without needing passwords.
What Happened?
OAuth, a widely used open-standard protocol for secure authorization, was the foundation of this attack. Instead of stealing passwords outright, attackers exploited OAuth’s token-based authentication mechanism to gain unauthorized access to sensitive data. The attack flow typically involved:
- Exploiting Trust: The attackers used compromised verified Microsoft Cloud Partner accounts to register malicious OAuth apps. The “verified” status made these apps appear legitimate, convincing users to grant them permissions.
- Phishing with Consent: Victims received phishing emails containing links to the malicious apps’ consent screens. These apps requested access to critical resources, such as emails, files, and calendars. Users who granted these permissions inadvertently handed attackers access tokens to their accounts.
- Token Misuse: With the tokens, attackers bypassed passwords entirely, gaining direct access to users’ Microsoft 365 accounts. This allowed them to:
- Send phishing emails internally to spread the attack further.
- Access and exfiltrate sensitive organizational data.
- Set up backdoors for persistent access.
Impact of the Breach
This breach was not limited to a single organization, it targeted a wide range of enterprises relying on Microsoft’s systems.
- High-Value Targets: Executives and decision-makers were the primary targets, enabling attackers to maximize the potential for lateral movement within networks.
- Access to Critical Resources: Permissions granted to malicious apps included reading emails, accessing OneDrive files, and even sending emails, posing risks of data exfiltration and fraud.
- Scope: Compromised accounts were used to target others within the same organizations, amplifying the attack’s scope.
Microsoft’s Response
Microsoft acted swiftly to contain the incident:
- Disabling Compromised Accounts: Verified partner accounts used for the attack were deactivated.
- Blocking Malicious Apps: Microsoft identified and removed the rogue OAuth applications from its platform.
- Strengthening App Verification: Enhanced app publisher verification processes were implemented to ensure only legitimate developers could register OAuth apps.
Lessons Learned
This incident highlights critical gaps in security measures and offers valuable lessons for organizations:
Restrict Third-Party App Access:
- Implement app consent policies that allow only pre-approved or verified apps.
- Regularly audit permissions granted to third-party apps.
Educate Employees:
- Train users to recognize and scrutinize consent requests, especially those asking for extensive permissions.
Adopt Zero Trust Principles:
- Enable conditional access policies to limit app access based on user roles, device states, and risk levels.
- Monitor OAuth activity for anomalies that could indicate malicious behaviour.
Implement Robust Incident Response:
- Quickly revoke access to suspicious apps and tokens.
- Conduct forensic investigations to identify the full extent of the compromise.
Conclusion
OAuth phishing is a growing threat, exploiting the trust we place in verified entities and the convenience of cloud-based applications. This incident is a stark reminder that even robust systems can be exploited if not rigorously secured. By understanding and addressing these vulnerabilities, organizations can improve their defenses and minimize the risk of falling victim to similar attacks.
