Navigating Identity Crisis: Rethinking Security Perimeters
TL;DR
AI-Driven Identity Crisis: Impersonation and Security Mandates
AI is automating impersonation by leveraging AI to:
- Craft phishing, smishing and vishing: Creating hyper-personalized emails that can be grammatically perfect, contextually aware and emotionally resonant. These messages no longer demonstrate the telltale signs of traditional phishing like broken English or generic greetings.
- Synthesize trust: Using voice-cloning AI to leave a quick, urgent voicemail from a trusted executive, bypassing the skepticism you’ve trained into your employees.
- Orchestrate multi-channel attacks: An attack might start with a benign-looking text, be followed up by a seemingly legitimate email and culminate in a phone call that seals the deal. Each step reinforces the fabricated identity.
- Exploit contextual awareness: With access to your data, AI can now analyze your communication patterns, typical working hours, frequent contacts and even your writing style to create messages that feel authentically “you.” They can reference recent meetings, ongoing projects or shared experiences scraped from internal communications or social platforms.
These capabilities aren’t theoretical — they’re operational today. AI-generated voice messages have been used to authorize fraudulent wire transfers. Sophisticated campaigns scrape social media profiles to create messages referencing colleagues or company projects.

Image courtesy of CSO Online
To combat this, security mandates must default to distrust. A dynamic, intelligent, and identity-centric model is required, emphasizing:
- Assume compromise: Operate as if the initial point of entry has already been breached. Prioritize rapid detection and response.
- Radical visibility: Unified visibility across every touchpoint, from the endpoint to the network core, is crucial. Focus on behavior to identify anomalies.
- Modernize authentication: Implement phishing-resistant authentication methods like FIDO2.
- Harness intelligence: Leverage broad, deep, and predictive threat intelligence. Understanding adversary tactics is paramount. Refer to resources like the annual Verizon Business Data Breach Investigations Report (DBIR).
The Rise of Agentic AI
Agentic AI has the potential to become an almost-independent threat actor. Given a simple goal, agentic agents can independently reason, plan and execute the complex, multi-step attack required to achieve malicious goals. Agentic AI can operate 24/7, adapt to obstacles in near real-time and scale its operations with terrifying efficiency.
When deploying AI agents, apply the principle of least privilege. Access to networks and data must be strictly circumscribed by its role and context, operating within a well-defined hierarchy. Implement clear guardrails, assign explicit limitations for each agent, and establish a process for immediate shutdown if agents operate outside defined parameters. Monitor and log every action, allowing for close reviews of any unusual behaviors. Maintain close human oversight over agent patterns and outcomes.
Continuously test the resilience of AI agents. Red teaming becomes critical, not just for infrastructure, but for autonomous systems, helping to verify that they cannot be tricked by an adversary.
Identity as the New Perimeter
The perimeter has eroded, creating trust issues within the security community. As of July 2023, 75% of breaches were caused by mismanaged identity, access, or privileges. In 2020, 79% of organizations reported an identity-related breach.
Authentication (who are you?) and authorization (are you allowed to do what you’re doing?) are key questions.
Nearly half of organizations use more than 25 systems to manage identity and access rights.
Historical Context and Evolution
Novell, founded in 1979, pioneered identity and access management with a file-sharing system that allowed admins and users to control access at the file level. At its peak in 1994, Novell grew to over $2 billion in annual revenue.
Microsoft's Active Directory (AD), previewed in 1999, became a fatal blow to Novell’s business. The Enron scandal and the Sarbanes-Oxley Act in 2002 led to increased demand for identity access management (IAM) solutions.
Todd McKinnon and Frederic Kerrest founded Okta in 2009, recognizing the limitations of on-prem identity tools and the challenges of migrating to a cloud version of Active Directory.
Policies like Bring your Own Device (BYOD) emerged, broadening the security landscape and accelerating new categories like mobile device management (MDM), customer identity and access management (CIAM), and machine and workload identity.
Current Market and Recent Breaches
The identity market is fragmented, with numerous vendors tackling different parts of the identity lifecycle. Despite this, over 60% of security leaders believed the space was consolidating as of August 2022.
4 out of 5 breaches start with an identity issue. Recent breaches have impacted firms like MGM, Caesar’s, Atlassian, and New Relic. Losses from these breaches can amount to hundreds of millions of dollars.
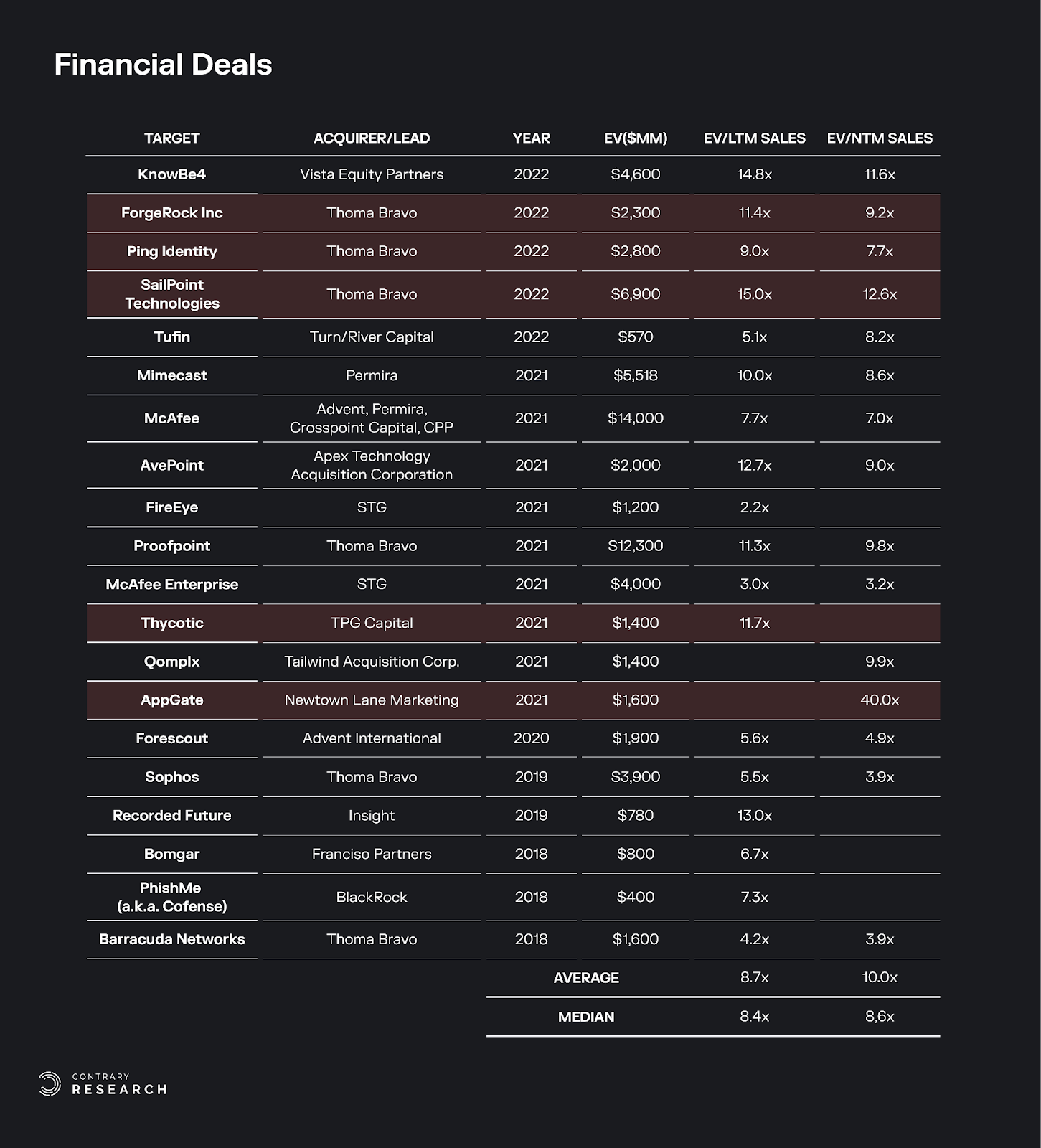
Image courtesy of Substack
Signs of an Identity Crisis
Questioning your basic understanding of who you are is a key sign. This includes questioning your character ("Am I a kind person?"), traits, and what matters most to you.
Other signs include:
- Feeling anxiety, agitation, or dissatisfaction with life.
- Changing yourself to suit any environment, situation, or relationship.
- Trouble answering questions about yourself.
- Not being able to trust that you can make good decisions.
To cope with an identity crisis:
- Express what’s important to you.
- Give yourself time for objectivity.
- Take care of yourself.
- Set firm boundaries and stick to them.
- Don’t fall into bad habits or destructive behaviors.
- Face your identity crisis squarely.
Consider seeking professional help for identity issues.


